Possible Alerts during the TWS installation or update
IBKR's Trader Workstation (TWS) is a global trading system enabling clients to use a suite of online trading tools. The TWS can be installed on Windows, Mac OS X and Linux, and it requires the presence of a Java Runtime Environment (JRE). Therefore, when you install the TWS, it also downloads the necessary Java files in order to run using a Java Virtual Machine (JVM).
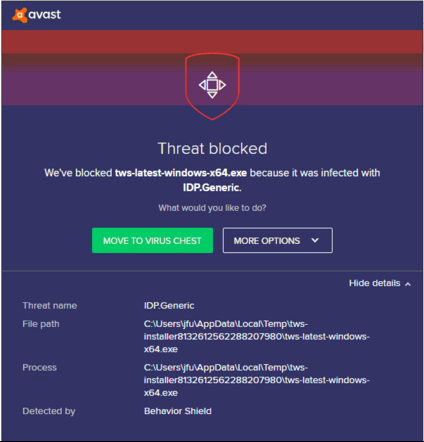
Sometimes, during the installation or update process of the TWS, software such as Antivirus applications will show an alert and prevent the process to complete. The warning and other messages in this case can safely be ignored, and you can complete the installation of the trading platform.
Table of content
Downloading the TWS installer and update patches
The TWS installers available in the download areas of ibkr.com or IBKR regional web sites are sealed and digitally signed using all the safety procedures required by the industry standards and do not contain any malicious code or process. The same industry standard practices have been used for the TWS update patches, which are automatically downloaded and installed when launching the TWS (if and only if there is an update available). Nevertheless, if you have received an alert, we recommend you to be cautious. Should you intend to keep the TWS installation file on your machine for future use, you should make sure that the same precautions for the protection of data from viruses and malware are applied to it.
Why do I receive a warning when I install the TWS or when the TWS automatic update runs?
You might see an alert (similar to Figure 1 but not limited to) and your security system would wait for your input on how to process the suspicious file. You usually have the option to quarantine the file, delete it, ignore it once or create a permanent exception for it.
Please note that your antivirus might autonomously quarantine or delete the TWS installer file or some of his components without asking for your confirmation and without showing you any warning. Nevertheless, this should only happen if you have preset your antivirus to specifically react in this way.
Figure 1.
What should I do when I receive a warning?
In case you receive a warning during the TWS installation or update, we recommend the following steps:
1. Delete the TWS installer and download it again from the IBKR main or regional web site
a) Delete the TWS installer file already present on your computer and then delete it as well from your Trash (empty your Trash)
b) From the table below, click on the TWS download area correspondent to your location
| Location | TWS download area |
| US | https://www.ibkr.com |
| Asia / Oceania | https://www.interactivebrokers.com.hk |
| India | https://www.interactivebrokers.co.in |
| Europe | https://www.interactivebrokers.co.uk https://www.interactivebrokers.eu |
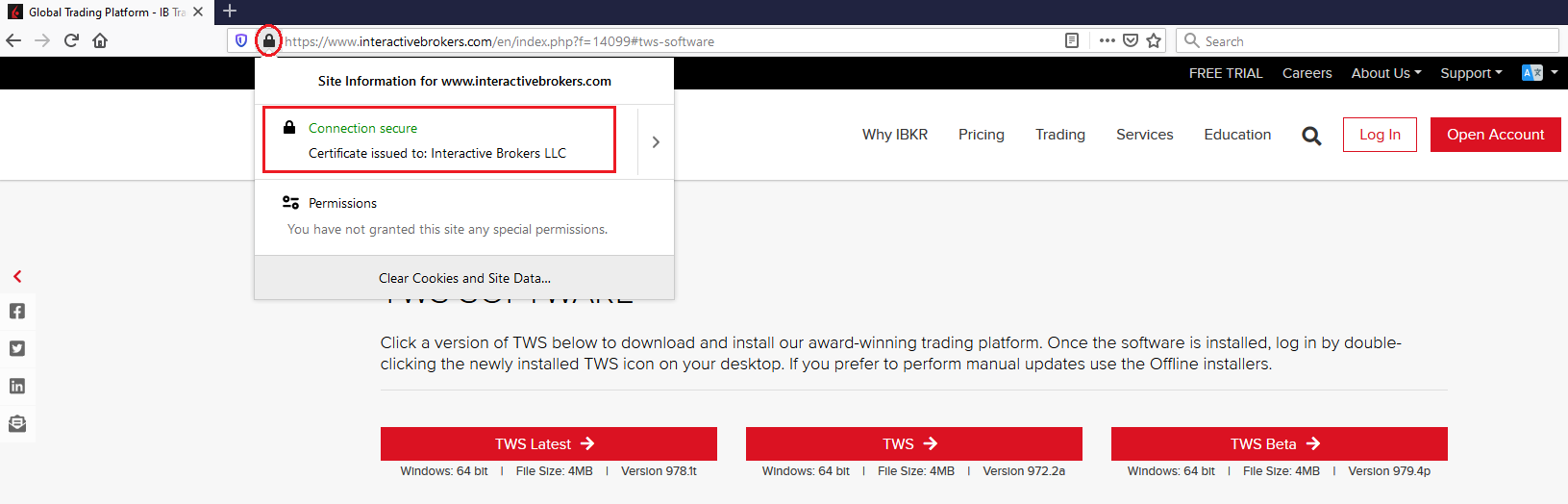
c) Check the website certificate. Most Internet browsers will immediately alert you in case the site certificate is invalid, compromised or expired. Nevertheless, if you want to check manually the validity of the site certificate, click on the padlock close to the address (URL) and make sure the Connection is reported as secure and no security warning are present (see Figure 2 below).
Figure 2.
d) Click on the button labeled with the TWS version you wish to use and download again the TWS installer
2. Check the digital signature of the TWS installer file you have downloaded
Normally you will immediately receive a security warning in case the digital signature of a file is compromised. Nevertheless, if you wish to perform a manual check, proceed as follows, according to your Operating System:
For Windows
a) From the Windows file explorer, access your Downloads folder or the folder where you placed the TWS installer
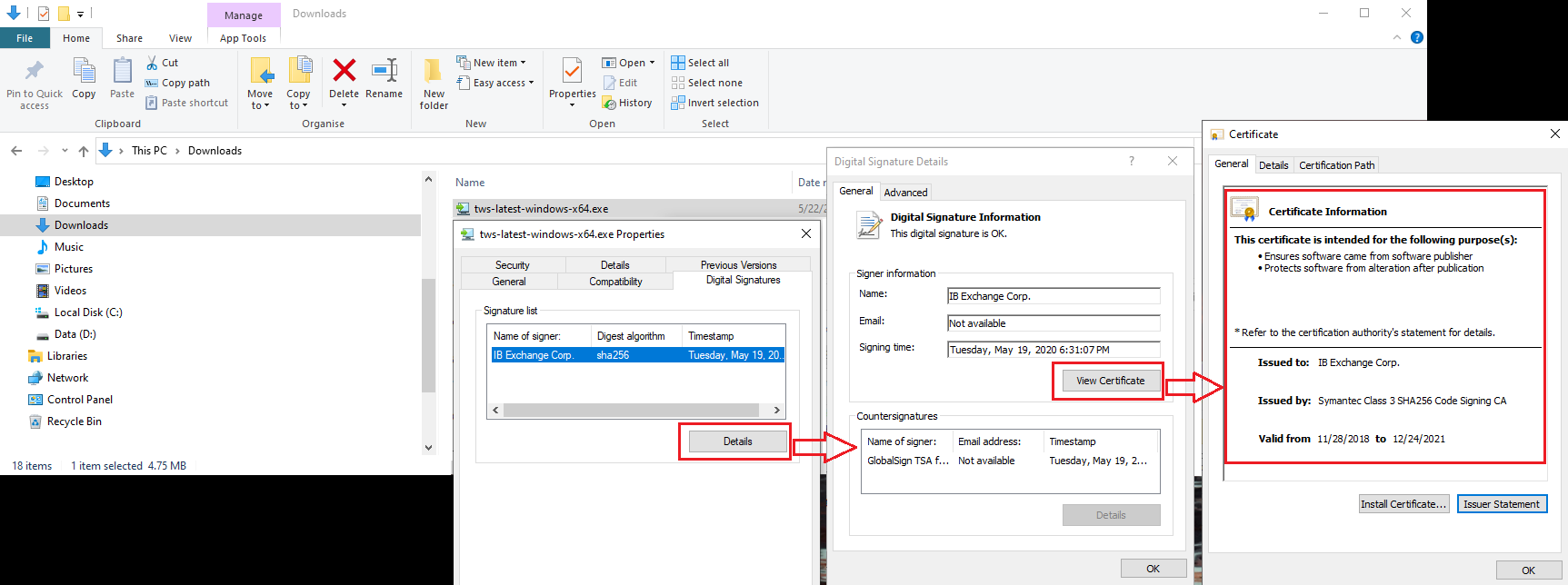
b) Right click on the TWS installer file, select Properties and then click on the tab "Digital Signatures"
c) Click on "Details" and on "View Certificate" to check the certificate status and signer. The legitimate signer is "IB Exchange Corp." (See Figure 3 below)
Figure 3.
For Mac OS X
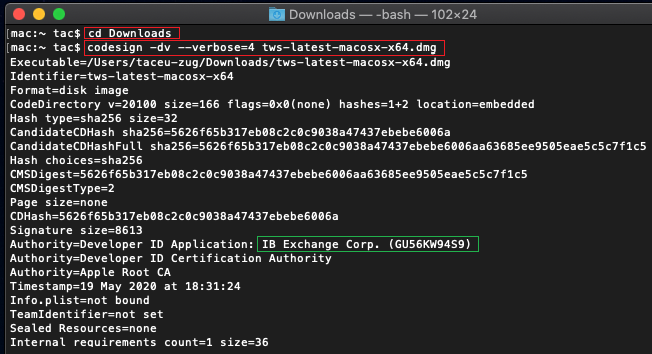
a) Click on the magnifier glass (Spotlight Search) on the top right of your screen and type Terminal. From the search results, launch the Terminal app
b) Type cd Downloads and press Enter
c) Type codesign -dv --verbose=4 tws-latest-macosx-x64.dmg and press Enter. Please notice that the name of the file (tws-latest-macosx-x64.dmg) may differ according to the TWS version you decided to download. If needed, replace the file name in the command with the appropriate one
d) Check the command output and make sure the "Developer ID Application" is "IB Exchange Corp." (see Figure 4 below)
Figure 4.
3. Run the TWS installer file you have downloaded
Once you have downloaded again the TWS installer and after you made sure the file is original (points 1. and 2. above), you can proceed with the installation. Should you still receive a warning from your antivirus, you can reasonably consider it as a false positive and ignore it. Should you need guidance on this step, please proceed directly to the next section.
How can I signal an Alert as false positive?
All modern security systems allow the creation of exceptions, precisely in order to address false positive cases. An exception is a rule forcing the antivirus engine not to scan a specific file or process. That specific file or process will hence be deemed safe and no further alerts will be raised for it.
The procedure for creating an exception may vary, according to the security software you are using. You may be able to create a temporary or permanent exception directly from the alert pop-up or you may have to create one manually from a specific section in the main configuration panel.
If you are unsure of the procedure, we recommend you to consult your antivirus documentation.
Once you have set an exception for the TWS installer file or for the TWS updater process, those will be no longer blocked and will be able to complete their respective tasks successfully.
What else can I do if I have doubts or if my system behaves abnormally?
If you have reasons to believe your machine may be compromised or infected, we recommend performing a full system scan. Usually you can right click on the antivirus icon present on the bottom taskbar (for Windows) or on the upper menu bar (for MacOS) and you will find the option to launch a full system scan. Alternatively, you may start that task from the main antivirus window. If you are unsure of the procedure, we recommend you to consult your antivirus documentation.
Technical Background
How does my security system scan the files I download from the Internet?
Modern antivirus and anti-malware engines base their threats recognition on:
Signature-based scanning: the antivirus scanner searches for a specific pattern of bytes that was previously catalogued as malicious or at least suspicious. The antivirus may check as well file signatures (called hash) against a database of known threats (called virus definitions).
Analysis of behavior: the antivirus engine detects specific actions which individually may not represent a threat but, when correlated together, resemble the usual activity of a malicious software (e.g. the ability of a code to replicate or hide itself, download additional files from the Internet, contact external hosts over the Internet, modify the Operating System registry) This type of scan is designed to detect previously unknown computer threats.
Heuristic detection: the scanner de-compiles the code or runs it within a virtual, restricted environment. It then classifies and weights the actions performed by the code against a predefined, behavior based, rule set.
Cloud-based protection and machine learning: those are relatively new techniques. The file that needs to be analyzed is sent to the antivirus / security system vendor cloud where sophisticated algorithms perform a deep analysis of the code authenticity and behavior.
Are those scan methods infallible?
Modern threats are very sophisticated and, like biological viruses, can mutate their code and their signatures. Moreover, new malwares and exploits are created every day and spread rapidly over the Internet. The threat recognition methods mentioned above are therefore not infallible but can guarantee a high percentage of malware recognition when combined together.
While signature based techniques are very successful in recognizing known threats and less prone to false positives, they are not so efficient in recognizing unknown malware or mutations of existing ones. In this area, the behavioral and heuristic methods perform much better although they are more prone to false positives since their detection is not based on bare code matching but on a certain degree of interpretation and hence uncertainty.
The term "false positive" is used when a security system classifies an innocuous file or process as malware.
Reference:
Alternative Streaming Quotes for US Equities
The SEC Vendor Display Rule requires that brokers give clients access to the NBBO at the point of order entry. In order to provide users with free live streaming market data, we cannot display this free stream when entering an order without the client subscribing to the paid NBBO. Please note, this does not apply to non-IBLLC clients.
Under the Rule 603(c) of Regulation NMS (Vendor Display Rule), when a broker is providing quotation information to clients that can be used to assess the current market or the quality of trade execution, reliance on non-consolidated market information as the source of that quotation would not be consistent with the Vendor Display Rule.
All clients (IBKR Lite and Pro) have access to streaming real-time US equity quotes from Cboe One and IEX at no charge. Since this data does not include all markets, we cannot show this quote when entering parameters for a US stock quote. Therefore and according to FINRA's enforcement of the SEC rule, IBKR provides IBLLC US clients a free default snapshot service, “US Snapshots VDR Required”. If clients do not sign up for an NBBO US equity data service and they are an IBLLC client, they will have access to free real-time snapshots when making trading decisions on US stocks. Order routing will not change based on what is shown on the screen. If one is subscribed to NBBO quotes or not, by default the trade will still take place with the assistance of the SMART order router designed to provide the best price for the order.
Please see the sample screenshots below from TWS Classic and TWS Mosaic for what occurs when placing an order without the NBBO streaming subscription for US equities.
TWS Classic:
1. Screenshot of quotes showing without order entry line item
2. Screenshot of quote going blank when putting in the order entry line item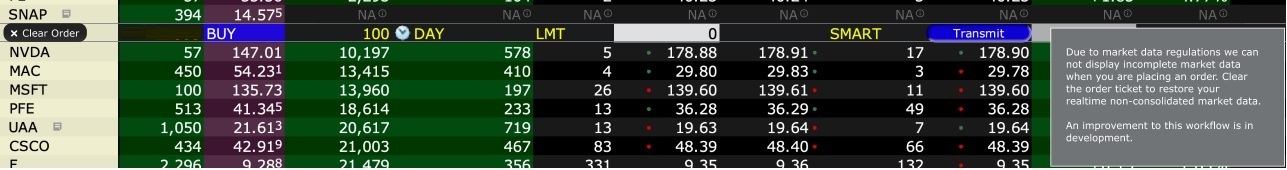
TWS Mosaic:
1. Screenshot of quotes showing without order entry line item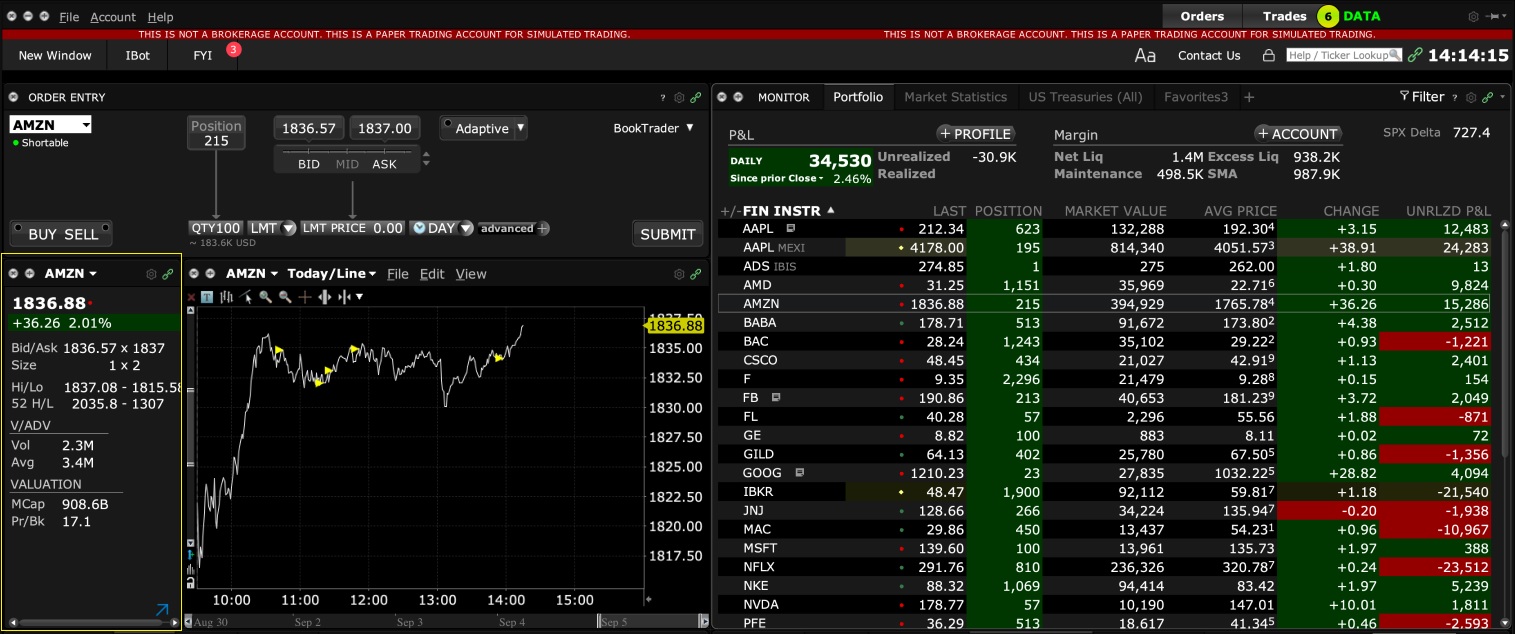
2. Screenshot of quote going blank when putting in the order entry line item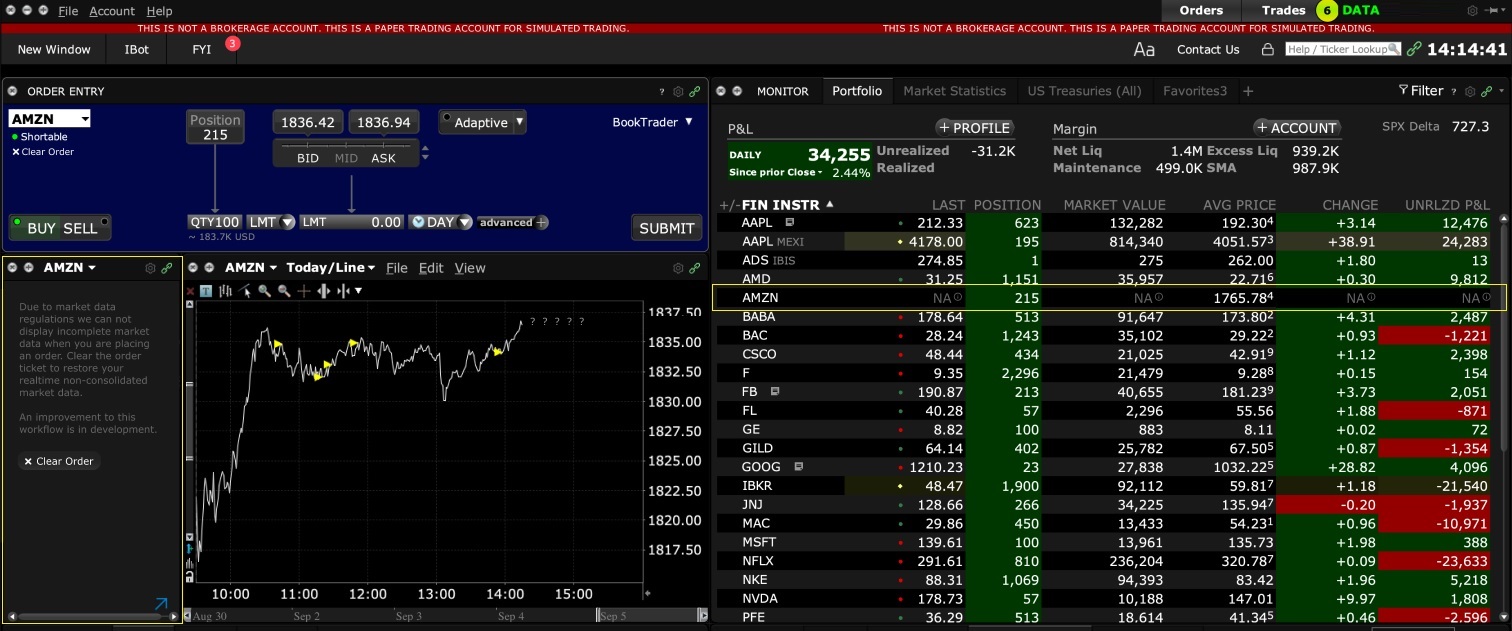
TWS / IB Gateway and their interaction with Proxy servers
Table of contents
Configuration instructions
- Can the TWS / IB Gateway operate through a Proxy server, and how?
- If I use a SOCKS Proxy server, do I need to configure the TWS / IB Gateway?
- If I use a SOCKS Proxy server, do I need to configure the client machines where TWS / IB Gateway runs?
- If I use a Web (HTTP) Proxy server, do I need to configure the TWS / IB Gateway?
- What alternatives do I have in case I cannot implement a proxy solution on my network?
Common issues
Technical Background
Configuration instructions
1. Can the TWS / IB Gateway operate through a Proxy?
Upon start-up and during the run-time, the TWS / IB Gateway must establish and maintain direct network connections to our gateways and market data servers1. Such connections are created from random local TCP ports (above 1024) and are directed to TCP ports 4000 and TCP 4001. Since those are not HTTP connections, they cannot be serviced by a Web (HTTP) Proxy. They can only be serviced by a SOCKS Proxy.
From within the TWS interface, you can access several external services, such as IBKR Client Portal, Statements, Contract details, Bond Search, etc. Those services, being web-based, can be accessed through a Web (HTTP) Proxy (see section 6 for details and configuration) or through a SOCKS Proxy (see sections 4. and 5. for details and configuration).
2. If I use a SOCKS Proxy server, do I need to configure the TWS / IB Gateway?
The TWS / IB Gateway does not contemplate an option for SOCKS proxy forwarding. Therefore, it does not have a place where an explicit SOCKS Proxy host/port can be configured. This does not mean that the TWS / IB Gateway cannot work with a Proxy. It simply means that the TWS / IB Gateway is unaware of the underlying SOCKS proxy setup (proxy-agnostic).
Important Note: While it is impossible for us to determine whether a Proxy is enabled on your network, we assure you that all IBKR platforms, including the TWS, do not impact nor influence your network configuration.
3. If I use a SOCKS Proxy server, do I need to configure the client machines where TWS / IB Gateway runs?
The connections started by the TWS / IB Gateway can be redirected to a SOCKS (Application) Proxy through a specific client machine setup. We mention some of them below. Please note that the final decision is yours and none of the below suggestions can be recommended by us as best adapted to your setup and requirements.
3a. Using a Proxy Client software installed on the client machine where TWS / IB Gateway is running
With this setup, the Proxy client will intercept the connections (not only HTTP but for other ports as well) initiated by the TWS / IB Gateway and redirect them to a SOCKS proxy server. The typical benefits of a transparent proxy include a standard enterprise configuration where all clients routed to the Internet will always be filtered and protected no matter what the end users do, or change, on their machines and the added benefit of reduction in typical user’s client-proxy configuration troubleshooting.
3b. Using a so-called Proxifier
This configuration is very similar to the one at point 5a with the only difference that the Proxifier software can be set to redirect to a Proxy all the requests started by a specific process (e.g., C:\Jts\tws.exe; C:\JTS\ibgateway\XYZ\ibgateway.exe), hence instating a process level packet forwarding instead of a port level forwarding. This setup allows handling environments where different proxy servers are used for different applications or where you would like to address a specific application requirement without modifying/disrupting the connectivity schema for other software installed. The advantage of this solution is minimal maintenance since the connectivity schema is bound to the process and not to the hosts/ports.
3c. Using specific network routing on a client machine
With this setup, you can modify the client machine standard network routes, adding new ones in order to forward packets with specific destinations (e.g., Order routing and Market Data servers1) to a different gateway.
This gateway will then be in charge of routing those requests to the destination hosts. This solution has as well the benefit of not modifying/disrupting the connectivity schema for other software installed but usually requires more maintenance on the gateway and on the client machine in case the IP of the destination servers are changed or in case new servers are added.
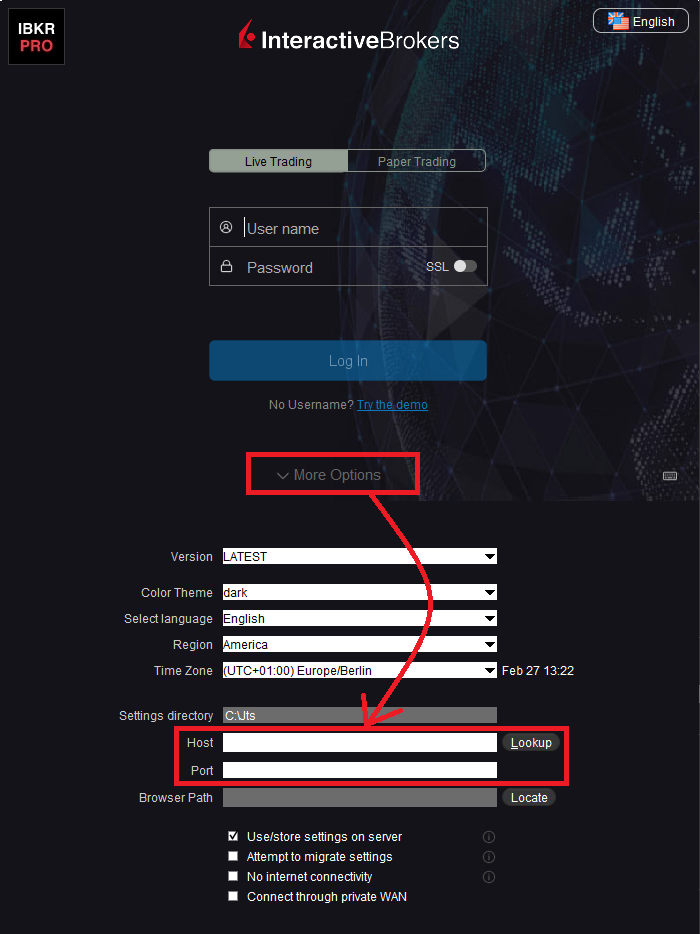
4. If I use a Web (HTTP) Proxy server, do I need to configure the TWS / IB Gateway?
If the Workstations on your local network access the Web content through a Web (HTTP) Proxy, you need to specify the Web Proxy IP Address and port. To do this, click More Options at the bottom of the TWS Login Screen, and enter your Proxy server details in the fields Host and Port (see Figure 1 below). The same fields are present in the IB Gateway Login Screen.
Figure 1.
The Web Proxy you set there will ONLY be used to fetch the web content accessible from within the TWS (e.g., Client Portal, Statements, Product Details, etc.)
5. What alternatives do I have in case I cannot implement a proxy solution on my network?
In this case, you might orient yourself towards a different type of access to the IBKR infrastructure, which includes a special connection type and a FIX/CTCI engine setup. This setup would, on the other hand, have different requirements in terms of commissions2.
Common Issues
6. What happens if the proxy configuration on your computer is wrong or outdated?
Occasionally, third-party software, even if already uninstalled, may leave behind a SOCKS proxy configuration on your computer. This may also happen if your computer has been infected with malware. In such cases, the proxy server, although configured, is non-existent or not accessible on the network. In such scenarios, the TWS will show an error message (e.g., No Internet Connectivity) and/or start the "Connection attempt #" loop upon login. The same will happen if the Proxy server exists, but has not been correctly configured on the client machines.
6a. How can I correct the proxy configuration if wrong?
When applicable, we recommend you always consult the IT / Networking team of your company first and ask for guidance.
If you are autonomously managing your network, please follow the instructions below according to the Operating System of your machine/s:
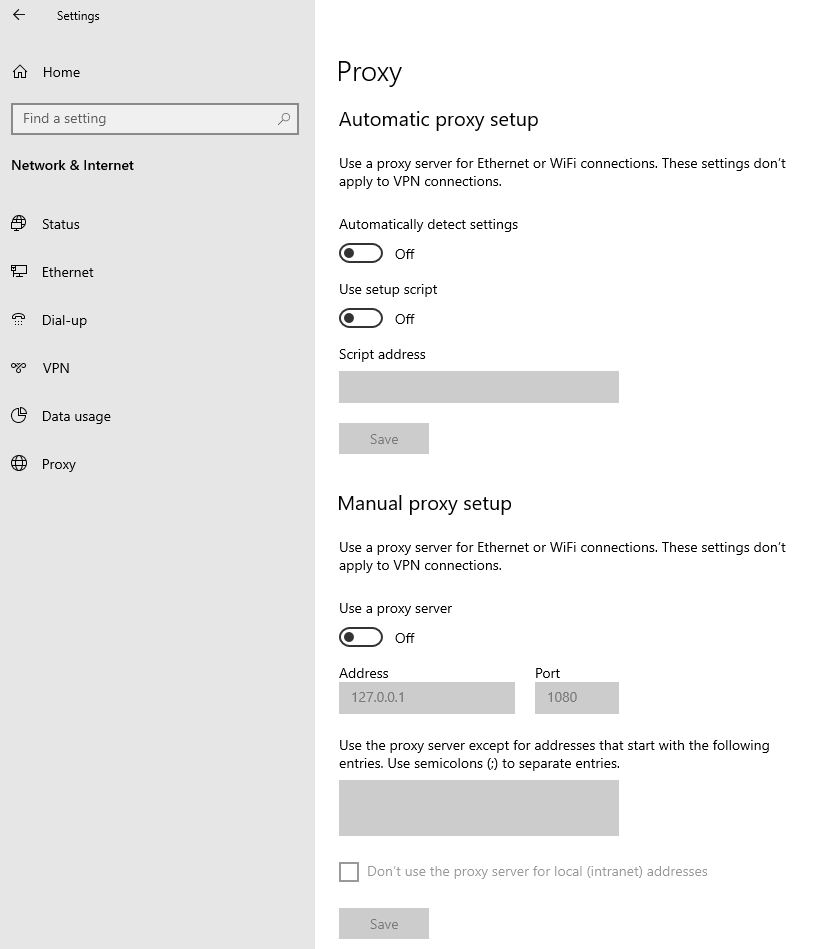
Windows
W.1 Press CTRL+S to open the Windows search
W.2 Type Proxy Settings and press Enter
W.3 If no Proxy is present on your network, make sure the switch "Use a proxy server" is deactivated (see Figure 2 below). If a Proxy server is active on your network, make sure the Address (or hostname) and Port are correctly defined.
Figure 2.
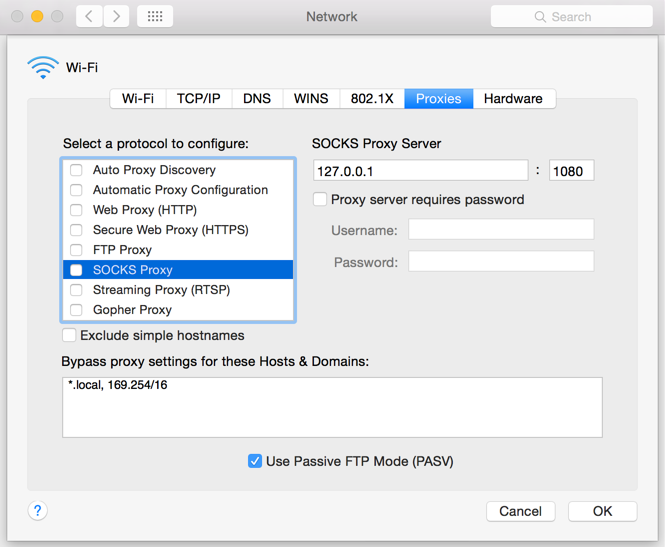
Mac
M.1 Click on the Apple icon at the top left corner of the screen and select System Preferences
M.2 Click on Network
M.3 Select the Network connection you are using to access the Internet (e.g. Wi-Fi) and click on it
M.4 Click on the Advanced button and then on the Proxies tab
5. If no proxy is present on your network, make sure all the checkboxes (SOCKS Proxy, Web Proxy, Secure Web Proxy) are deactivated (see Figure 3 below). If a Proxy is present on your network, ensure the Protocol, Address (or hostname) and Port are correct.
Figure 3.
7. You are using Public proxies and proxy chains to hide your presence or identity
There are public proxy and proxy chain services purposed to disguise or hide the identity and the activity of the subscriber or to bypass regional restrictions. One of the most famous services is the "Tor" network.
While those services may not necessarily be used for criminal purposes, they render subscriber traceability very difficult when not impossible. Since IBKR is obliged by the financial industry regulators to maintain records of trading activities and trade initiators, we do not allow our clients to reach our systems while using an anonymizing service. If you are using such a service, your TWS connection attempts will be automatically rejected by our gateways.
Technical Background
A proxy server usually acts as a gateway and as a barrier between your local network and the Internet. The proxy listens for outgoing connection requests from the internal workstation/s and forwards them to the desired target host or service on the Internet. When the target replies to such requests, the proxy routes the incoming responses back to the internal workstation/s that initiated the process.
Being the proxy, the only machine of your network actually accessing the Internet, it prevents the other machines and the internal segment of your network (LAN) from being accessible by external actors and hence from being exposed to threats and intrusion attempts.
Additionally, a proxy server can offer a variety of other services, such as web content caching and filtering.
9. Which types of Proxy servers are commonly used and where?
Proxy servers are commonly found within enterprise-grade networks. In the vast majority of cases, proxies are not used by individuals since private broadband connections are established through consumer-grade routers that already offer built-in proxy/firewall solutions. An exception is represented by public proxy or proxy chains discussed in detail in the section You are using Public proxies and proxy chains to hide your presence or identity
There are two main types of Proxy servers:
The HTTP (Hypertext Transfer Protocol) defines the rules and the standards for fetching Web content from a Web server and rendering such content on your Web Browser.
A Web Proxy handles only the routing of HTTP requests and HTTP responses. Those requests are transparently generated and sent by your browser whenever you access a Web page. Such requests are normally sent using specific ports (TCP 80 and TCP 443). Hence a Web Proxy usually listens for outgoing HTTP requests coming from your internal network (LAN) only on the TCP ports mentioned above.
SOCKS (Socket Secure) Proxies are designed to handle any type of traffic (not only HTTP/S traffic), generated by any protocol or program (including Trader Workstation).
Notes
1. More information about the servers accessed by the TWS is available in IBKB2816.
2. For an overview of the different special connection options and related requirements, please click here.
For an overview of the FIX infrastructure, please click here.
How to download and install the IBKR Mobile app from alternative app stores
As a consequence of the US Government Huawei ban, the owners of Huawei smartphones will be no longer able to access the Google Play Store and download app from there. If you are affected by this constraint, you will still be able to download and install the IBKR Mobile app from an alternative app store.
Please proceed as follows:
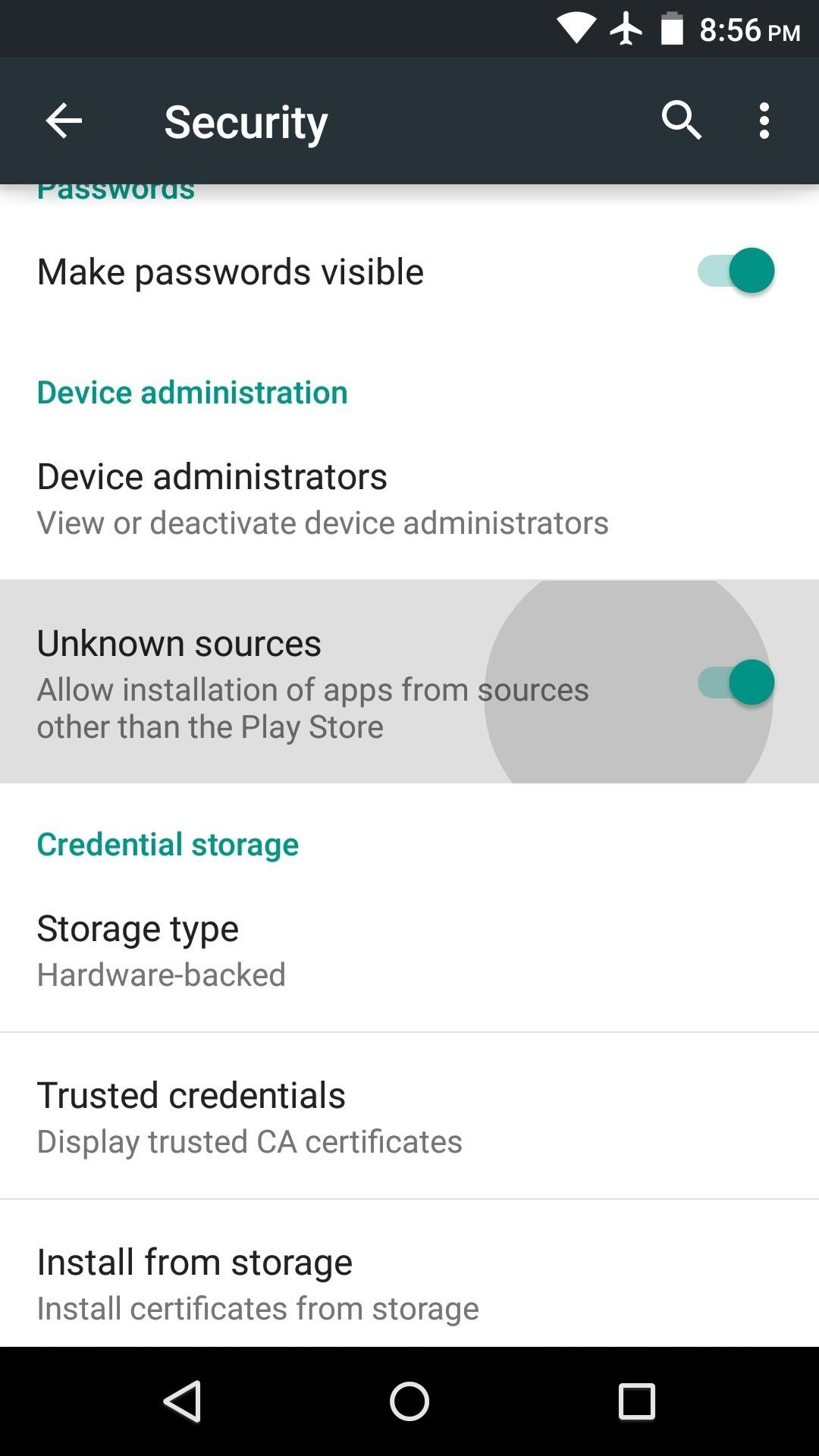
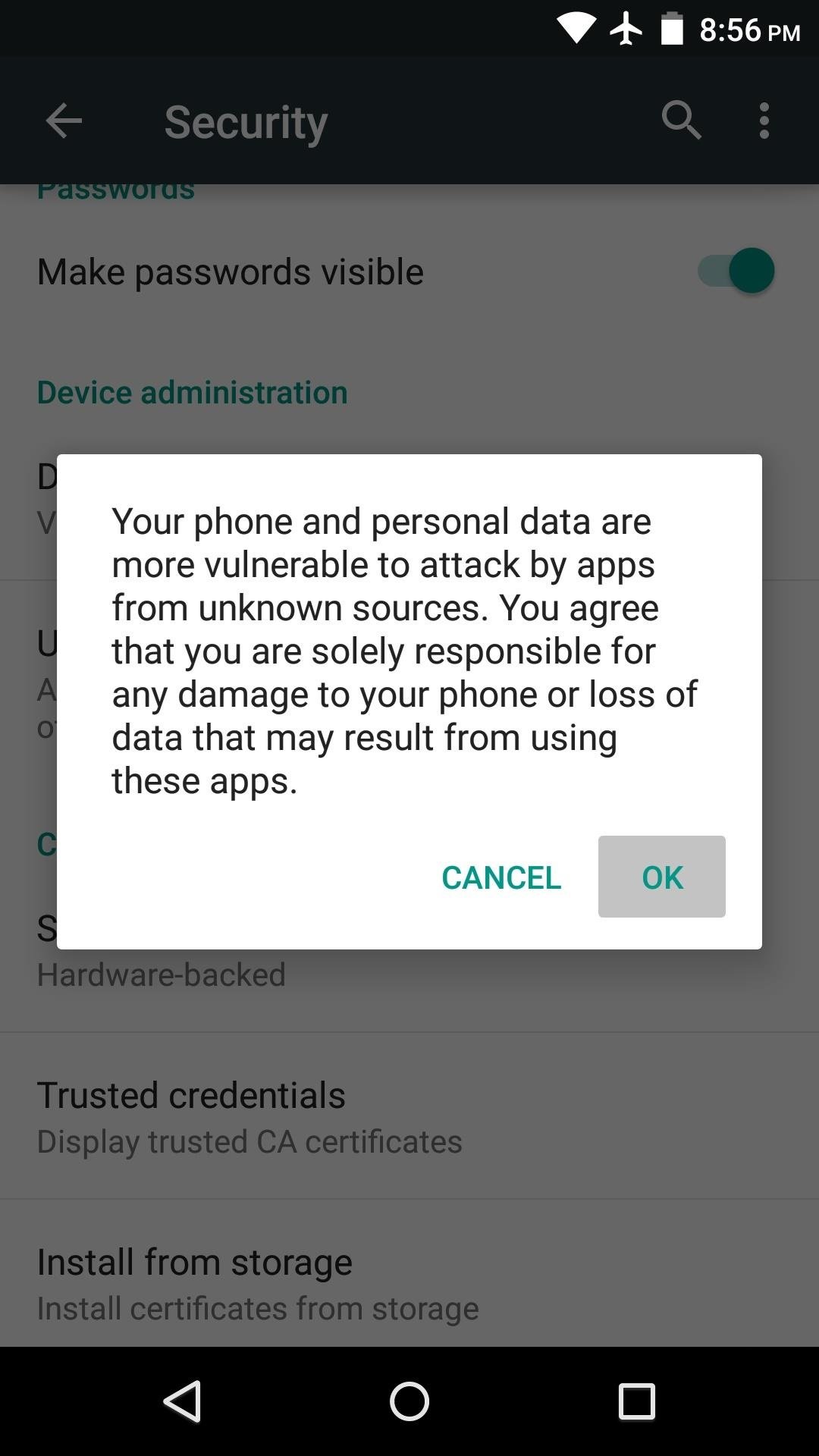
A) Allow your phone to install software from alternative app stores in this way:

2) Under the section System you will find the item Security (it can be called Lock Screen and Security). Click on it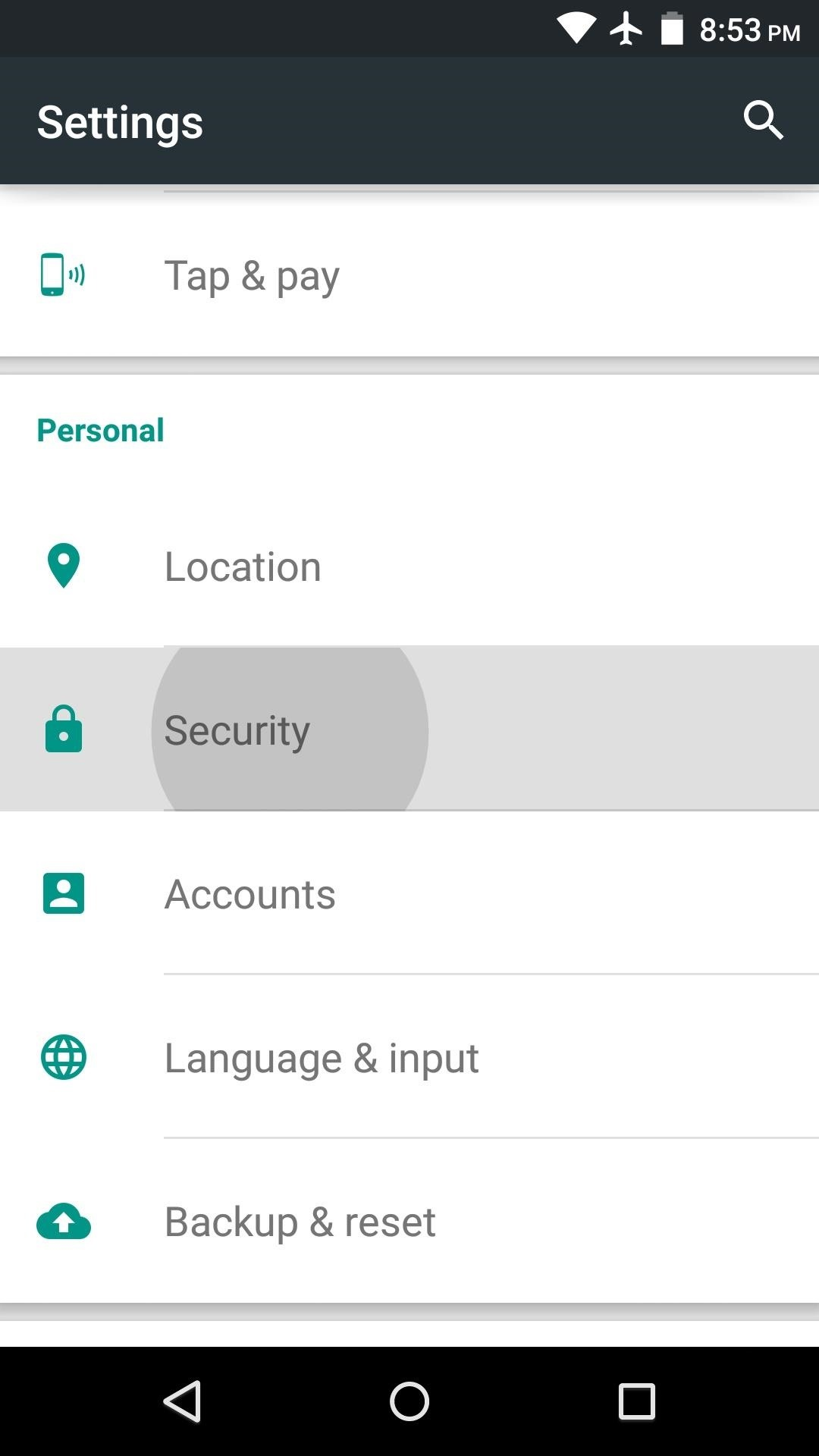
B) You can now download the IBKR Mobile by clicking on one of the links below, according to the alternative store you want to use:
360.cn
.png)
Baidu
Datos de mercado en instantánea
ANTECEDENTES
IBKR ofrece a los clientes elegibles la posibilidad de solicitar cotizaciones de precios en tiempo real de un único instrumento. Este servicio, denominado 'Cotizaciones en instantánea', es distinto al servicio de cotizaciones tradicionales, dado que ofrece un servicio en streaming y actualizaciones de los precios en tiempo real. Las cotizaciones en instantánea se ofrecen como una alternativa de bajo coste para aquellos clientes que no realizan operaciones con regularidad y no desean depender de las cotizaciones en diferido1al enviar órdenes. A continuación se facilita más información sobre este servicio de cotizaciones.
COMPONENTES DE LA COTIZACIÓN
En cada cotización en instantánea se facilitan los datos siguientes:
- Último precio
- Último volumen
- Último mercado
- Bid y ask actuales
- Volumen por cada bid y ask actuales
- Mercado por cada bid y ask actuales
SERVICIOS DISPONIBLES
| Servicio | Restricciones | Precio por solicitud de cotización (USD)2 |
|---|---|---|
| AMEX (Network B/CTA) | 0.01 $ | |
| Total ASX | Sin acceso a ASX24. Limitado a suscriptores no profesionales |
0.03 $ |
| Bolsa de Madrid | 0.03 $ | |
| Canadian Exchange Group (TSX/TSXV) | Limitado a suscriptores no profesionales que no son clientes de IB Canada | 0.03 $ |
| CBOT en tiempo real | 0.03 $ | |
| CME en tiempo real | 0.03 $ | |
| COMEX en tiempo real | 0.03 $ | |
| Eurex Core | Limitado a suscriptores no profesionales | 0.03 $ |
| Euronext Basic | Limitado a suscriptores no profesionales Incluye títulos, índices, derivados basados en acciones y derivados basados en índices de Euronext. |
0.03 $ |
| ETF e índices de Alemania | Limitado a suscriptores no profesionales | 0.03 $ |
| Derivados de Hong Kong (HKFE) | 0.03 $ | |
| Mercado de valores de Hong Kong (acciones, warrants, bonos) | 0.03 $ | |
| Mercado de Johannesburgo | 0.03 $ | |
| Derivados de Montreal | Limitado a suscriptores no profesionales | 0.03 $ |
| NASDAQ (Network C/UTP) | 0.01 $ | |
| Derivados nórdicos | 0.03 $ | |
| Acciones nórdicas | 0.03 $ | |
| NYMEX en tiempo real | 0.03 $ | |
| NYSE (Network A/CTA) | 0.01 $ | |
| OPRA (Mercados de opciones de EE. UU.) | 0.03 $ | |
| Mercado de valores de Shanghái, instantánea de 5 segundos (mediante HKEx) | 0.03 $ | |
| Bolsa de Shenzhen, instantánea de 3 segundos (mediante HKEx) | 0.03 $ | |
| SIX Swiss Exchange | Limitado a suscriptores no profesionales | 0.03 $ |
| Mercado al contado de Alemania (Frankfurt/Xetra) | Limitado a suscriptores no profesionales | 0.03 $ |
| STOXX, datos sobre índices en tiempo real | Limitado a suscriptores no profesionales | 0.03 $ |
| Bolsa de Toronto | Limitado a suscriptores no profesionales que son clientes de IB Canada | 0.03 $ |
| TSX Venture Exchange | Limitado a suscriptores no profesionales que son clientes de IB Canada | 0.03 $ |
| UK LSE (IOB) Equities | 0.03 $ | |
| UK LSE Equities | 0.03 $ |
1De conformidad con los requisitos normativos, IBKR ya no ofrece información de cotizaciones en diferido sobre acciones estadounidense a los clientes de Interactive Brokers LLC.
2El coste es por solicitud de cotización en instantánea y se calculará en el equivalente a la divisa base, en caso de que esta no sea en USD.
ELEGIBILIDAD
- Las cuentas han de mantener el mínimo de suscripciones a datos de mercado y cumplir con los requisitos de saldo respecto de la liquidez de mantenimiento a fin de poder calificarse para solicitar cotizaciones en instantánea.
- Los usuarios han de utilizar una versión de TWS 976.0 o superior para acceder a la función de cotizaciones en instantánea.
INFORMACIÓN SOBRE LA TARIFICACIÓN
- Los clientes recibirán $1.00 de cotizaciones en instantánea de forma gratuita cada mes. Las instantáneas gratuitas se podrán aplicar a solicitudes de cotizaciones estadounidenses o no estadounidenses y se aplicarán cargos, sin previo aviso, una vez que se haya agotado la asignación gratuita. Los clientes pueden revisar su uso de cotizaciones en instantánea al cierre de cada día hábil mediante el Client Portal.
- Las tarifas de las cotizaciones generalmente se calculan durante la primera semana del mes siguiente en el que se solicitaron los servicios de cotizaciones en instantánea. Las cuentas que no dispongan de suficiente efectivo o de capital con valor de préstamo para cubrir la tarifa mensual estarán sujetas a liquidaciones de posiciones.
- La tarifa mensual para las instantáneas tendrá un límite equivalente al precio mensual del servicio de streaming en tiempo real que corresponda. Una vez alcanzado dicho límite, las cotizaciones en streaming se proporcionarán sin coste adicional durante el resto del mes. El cambio a las cotizaciones en streaming se produce generalmente a las 18:30, hora del este, del día siguiente, una vez se ha llegado al umbral de cotizaciones en instantánea. Al cerrar del mes, se terminará el servicio en streaming y se restablecerá el contador de cotizaciones en instantánea. Cada servicio tiene un límite independiente y, por tanto las solicitudes de cotizaciones para un servicio no se tendrán en cuenta para el límite del otro servicio. Consulte la tabla que aparece a continuación para ver algunos ejemplos.
| Servicio | Precio por solicitud de cotización (USD) | Límite para suscriptores no profesionales (solicitudes/importe total)2 | Límite para suscriptores profesionales (solicitudes/importe total)3 |
|---|---|---|---|
| AMEX (Network B/CTA) | 0.01 $ | 150/1.50 $ | 2,300/23.00 $ |
| NASDAQ (Network C/UTP) | 0.01 $ | 150/1.50 $ | 2,500/$25.00 |
| NYSE (Network A/CTA) | 0.01 $ | 150/1.50 $ | 4,500/$45.00 |
SOLICITUD DE COTIZACIONES EN INSTANTÁNEA
Negociación de escritorio - TWS (Clásica):
Si dispone de la opción de visualización de datos en diferido y está suscrito a los permisos en instantánea, en la columna Acción del ticker se mostrará el botón de Instantánea:
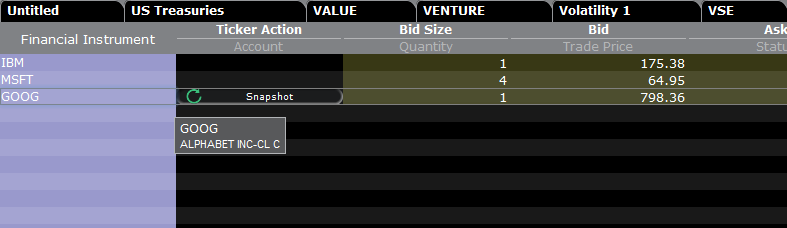
Al hacer clic en el botón de Instantánea, se mostrará una ventana de detalles de cotización. En la ventana de detalles de cotización se generará una marca de tiempo en el momento en el que se reciba la cotización NBBO para el símbolo en cuestión, junto con la información NBBO:
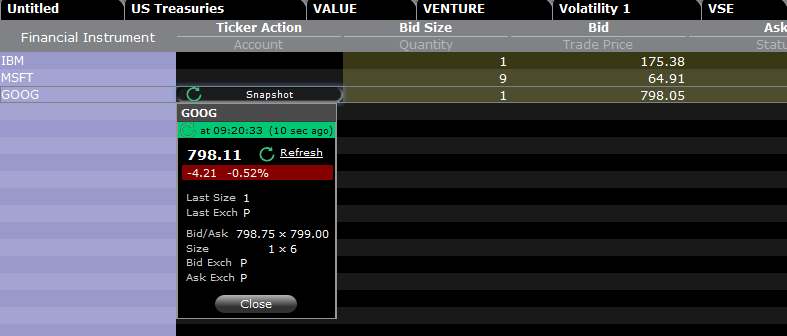
Si hace clic en el enlace Actualizar de la ventana de detalles de cotización, se actualizará la cotización NBBO.
Ejemplo:
En el caso anterior, GOOG es una acción cotizada en NASDAQ (Network C/UTP). Se aplicará un cobro de 0.01 USD por solicitud (es decir, por instantánea).
- Los clientes no profesionales pueden solicitar 149 instantáneas más para GOOG o para cualquier acción cotizada en NASDAQ (Network C/UTP) antes de que se conviertan en cotizaciones en streaming.
- Los clientes profesionales pueden solicitar 2 499 instantáneas más para GOOG o para cualquier acción cotizada en NASDAQ (Network C/UTP) antes de que se conviertan en cotizaciones en streaming.
Solo se cobrarán las instantáneas hasta llegar al límite de precio. Una vez se haya llegado al limite de instantáneas, no se aplicará ningún cargo durante el resto del mes y empezará a recibir cotizaciones en instantánea para este servicio.
Negociación de escritorio - TWS (Mosaico):
Si dispone de la opción de visualización de datos en diferido y está suscrito a los permisos en instantánea, al seleccionar una fila en la pestaña de seguimiento de actividad, en la ventana de entrada de órdenes se mostrará una opción para solicitar una cotización en instantánea.
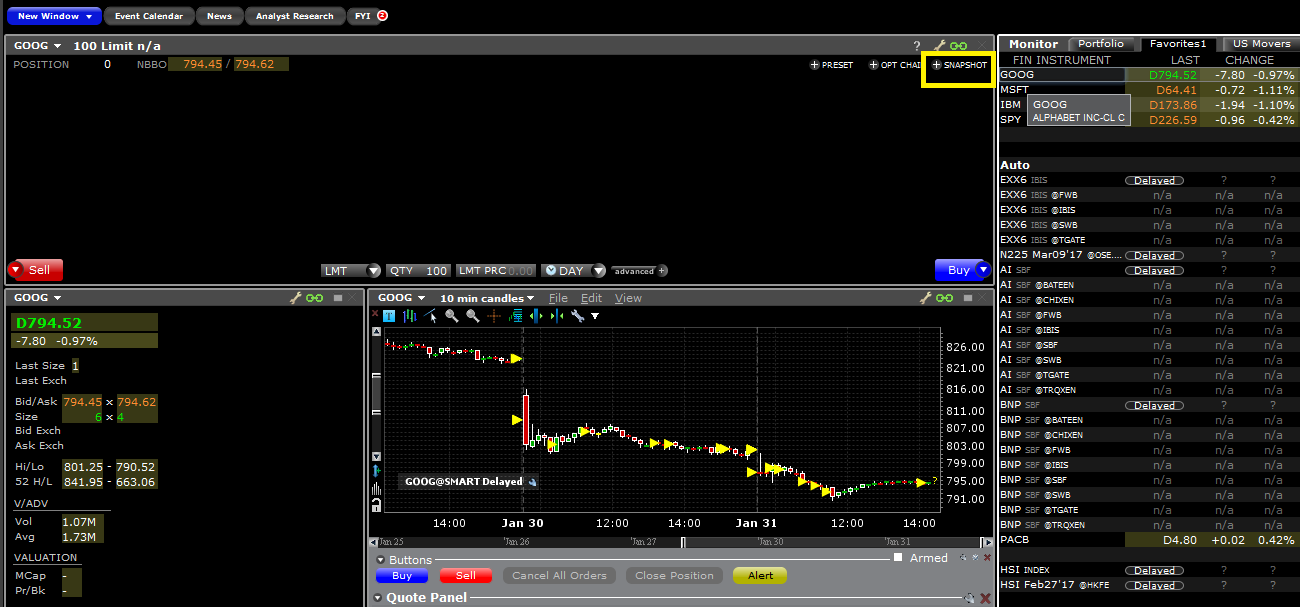
Al hacer clic en el enlace +INSTANTÁNEA, se mostrará una ventana de detalles de cotización. En la ventana de detalles de cotización se generará una marca de tiempo en el momento en el que se reciba la cotización NBBO para el símbolo en cuestión y generará la información NBBO:
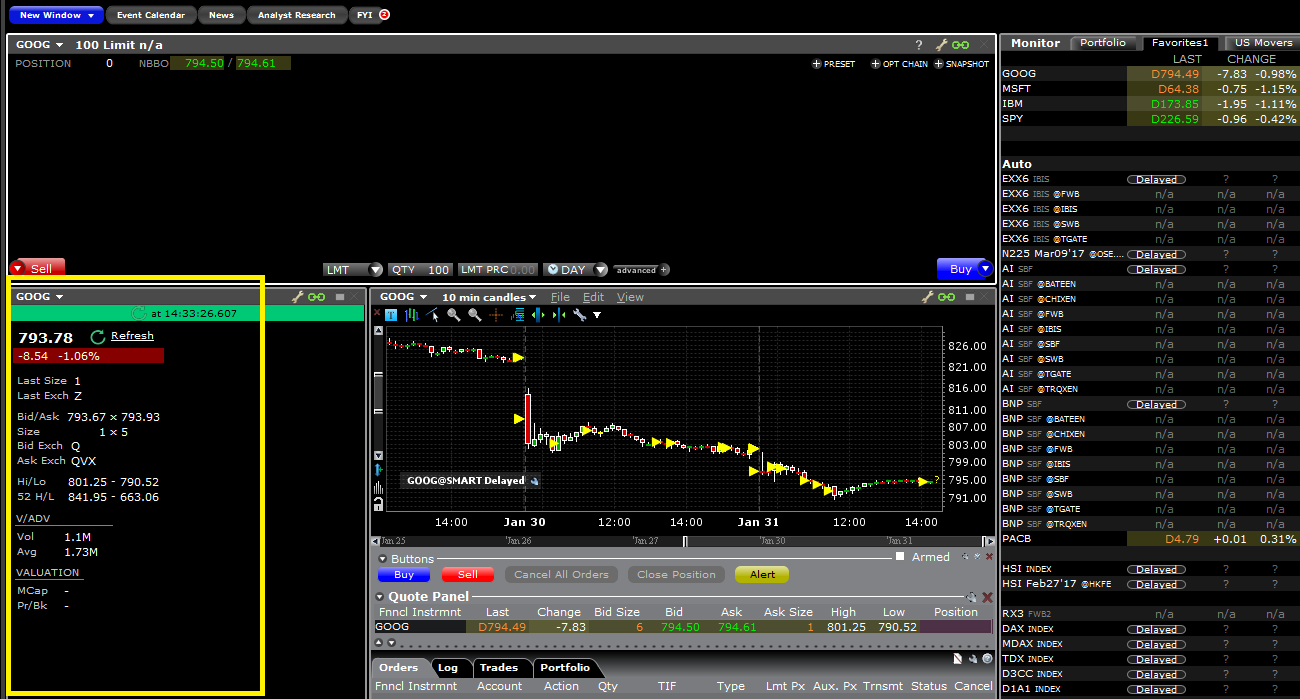
Al hacer clic en el enlace Actualizar de la ventana de detalles de cotización, se actualizará la cotización NBBO.
Client Portal:
Si dispone de la opción de visualización de datos en diferido y está suscrito a los permisos en instantánea, en la ventana de tiques de órdenes, debajo del precio bid y ask, se mostrará un enlace para Instantáneas:
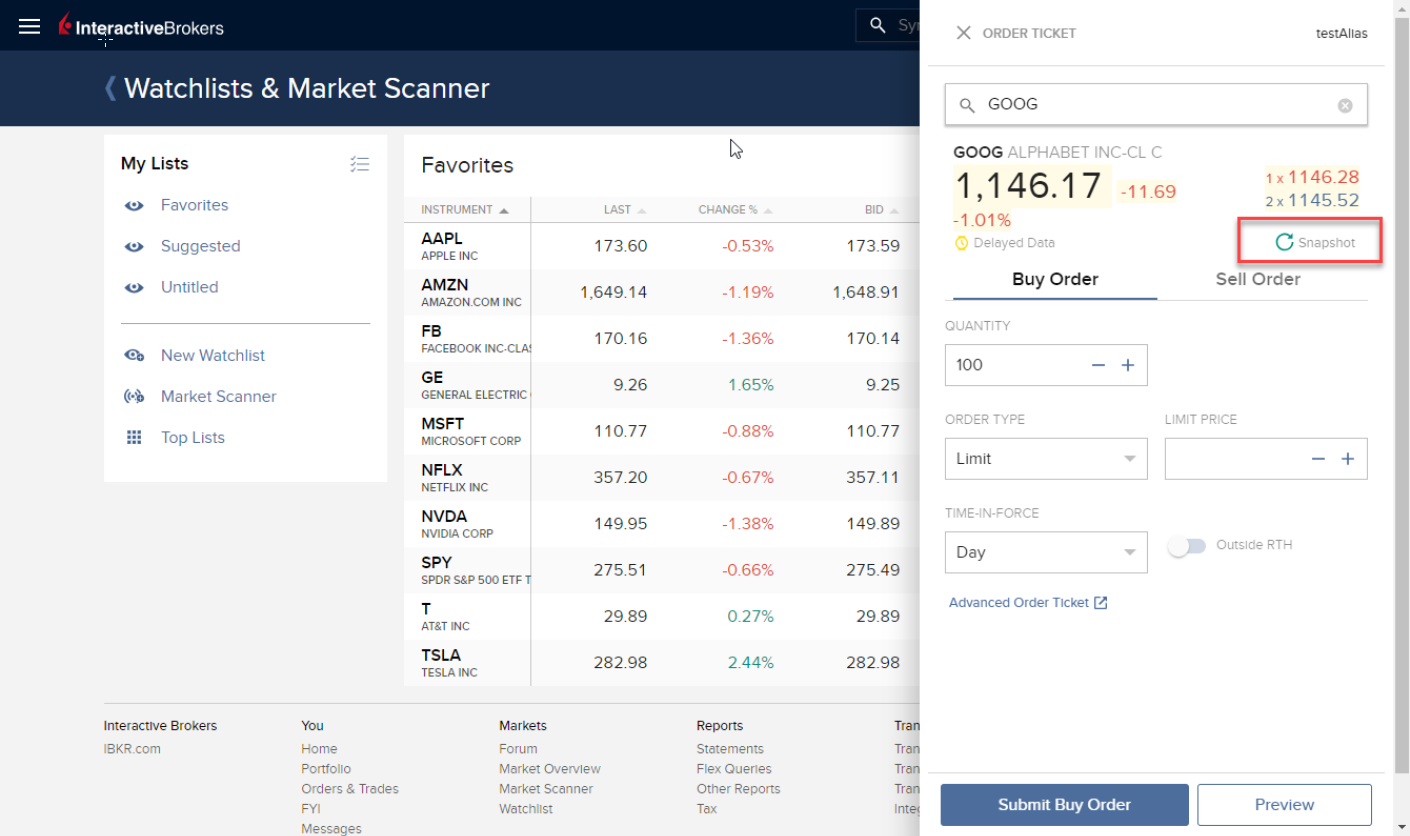
Al hacer clic en el enlace Instantánea se mostrará una ventana de detalles de cotización. En la ventana de detalles de cotización se generará una marca de tiempo en el momento en el que se reciba la cotización NBBO para el símbolo en cuestión:
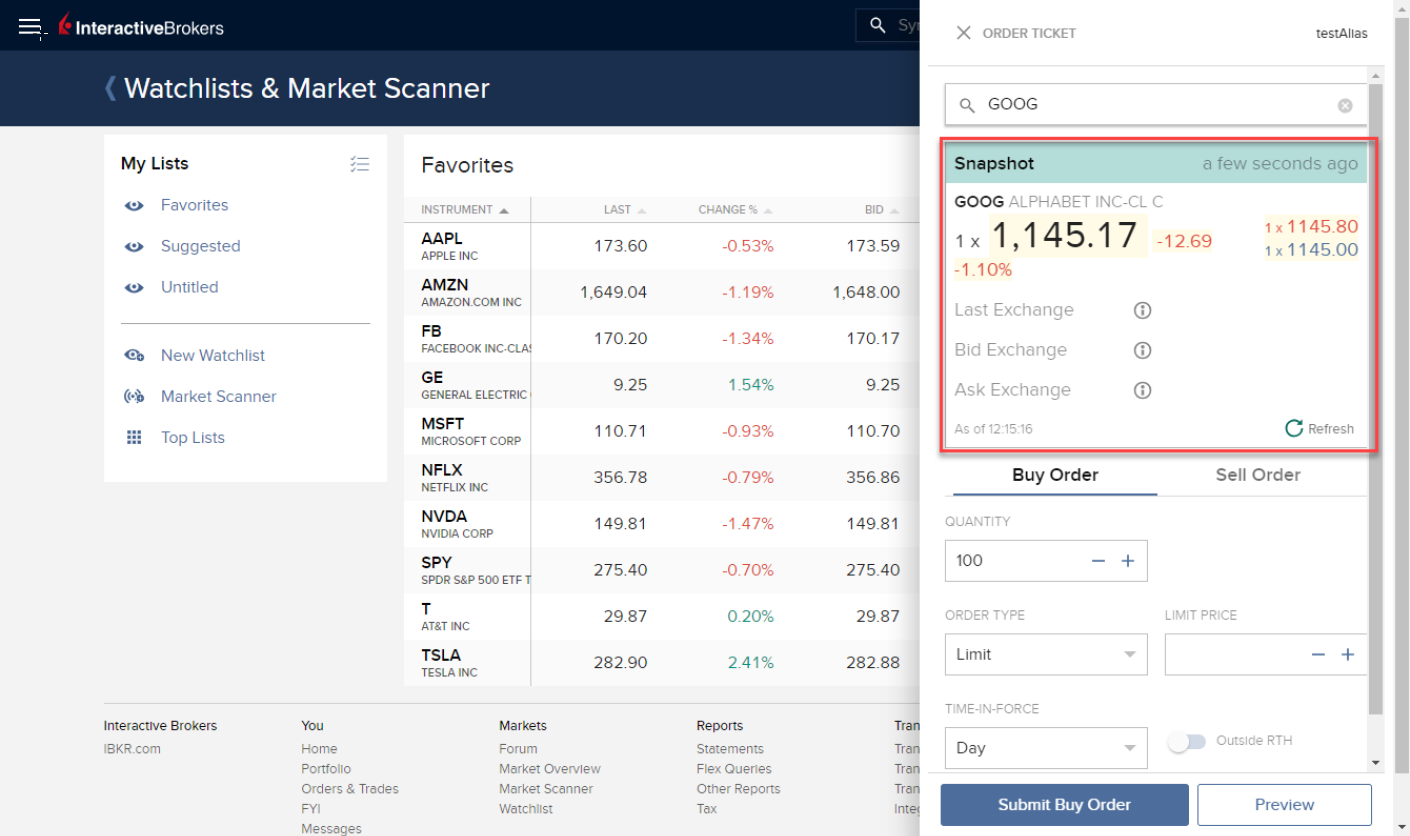
Al hacer clic en el enlace Actualizar de la ventana de instantáneas se actualizará la cotización NBBO.
Negociación web - WebTrader:
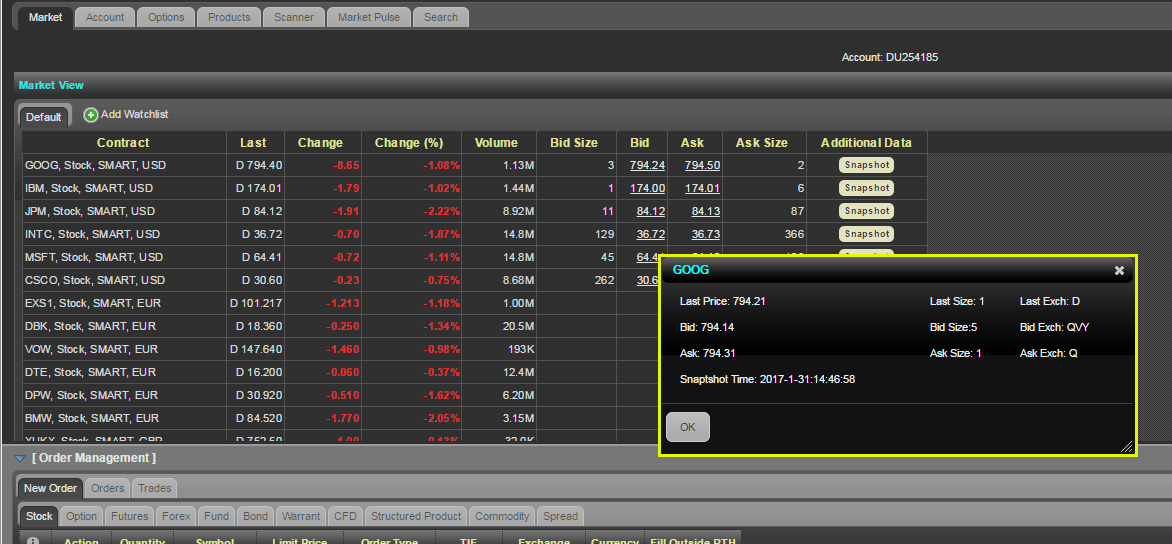
Si dispone de la opción de visualización de datos en diferido y está suscrito a los permisos en instantánea, en la pestaña de mercado, debajo de la columna de datos adicionales se mostrará un botón para instantáneas:
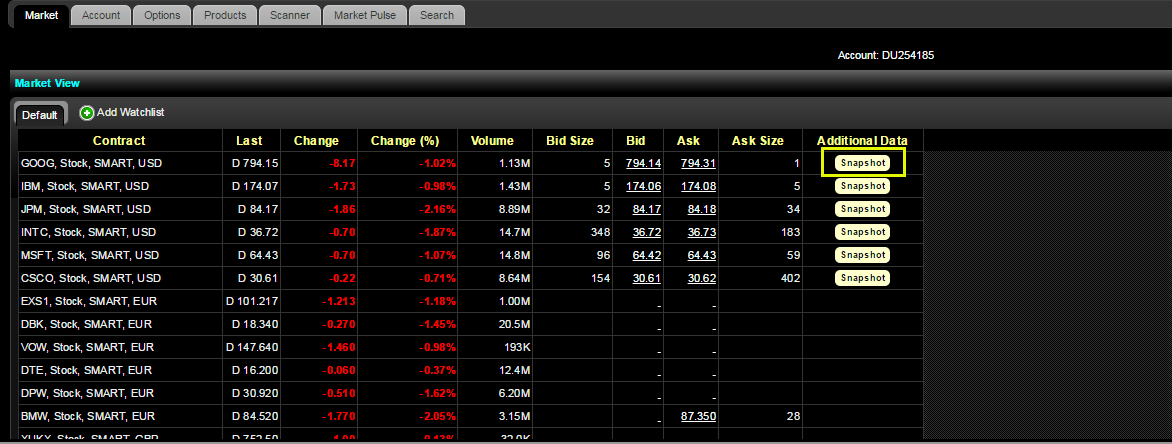
Al hacer clic en el botón instantánea se mostrará una ventana de detalles de cotización. En la ventana de detalles de cotización se generará una marca de tiempo en el momento en el que se reciba la cotización NBBO para el símbolo en cuestión:
Negociación móvil - IBKR Mobile:
En la pantalla de cotización se mostrará un cuadro de cotización cada vez que se pulse en un símbolo. Si dispone de la opción de visualización de datos en diferido y está suscrito a los permisos en instantánea, se mostrará un enlace para instantáneas:
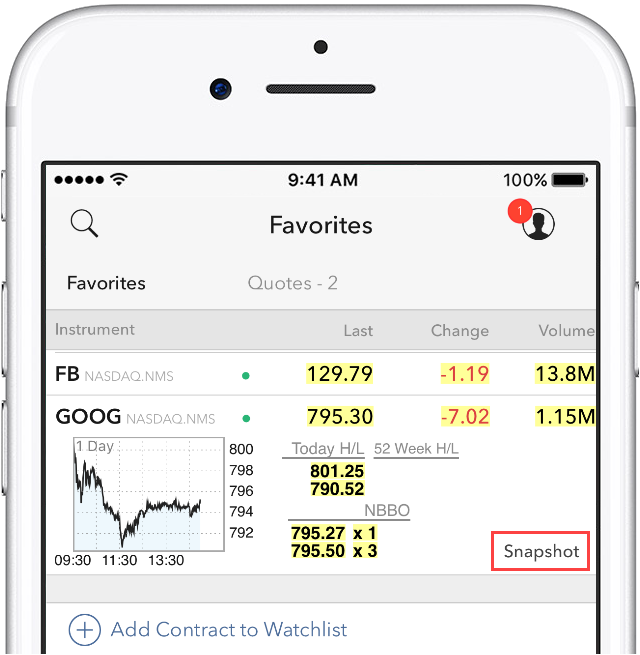
Al pulsar el botón de instantánea se mostrará una ventana de detalles de cotización. En la ventana de detalles de cotización se generará una marca de tiempo en el momento en el que se reciba la cotización NBBO para el símbolo en cuestión, junto con la información NBBO:

Why do I receive a message stating market data is over the limit?
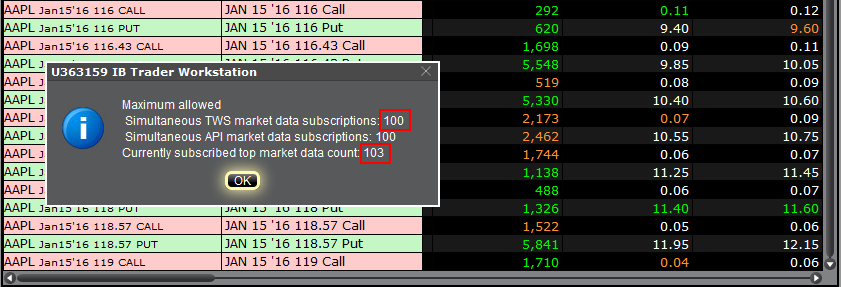
When you open an account with IBKR, you are initially set to receive a minimum of 100 concurrent lines of market data. This means that, either on IBKR Trading Platforms (TWS, IBKR Mobile, Client Portal trading facility) or on API/third party interface, you can simultaneously feed 100 tickers with market data. As explained here, after the first month of trading, your allowance might be increased either automatically (based on your account equity/commission) or manually (by the purchase of Quote Booster packs.)
Note: The same market data allowance is set for all the users of the same account, since it is based on account-wise parameters such as commissions and equities.
Table of contents
Why some financial instruments show question marks instead of data?
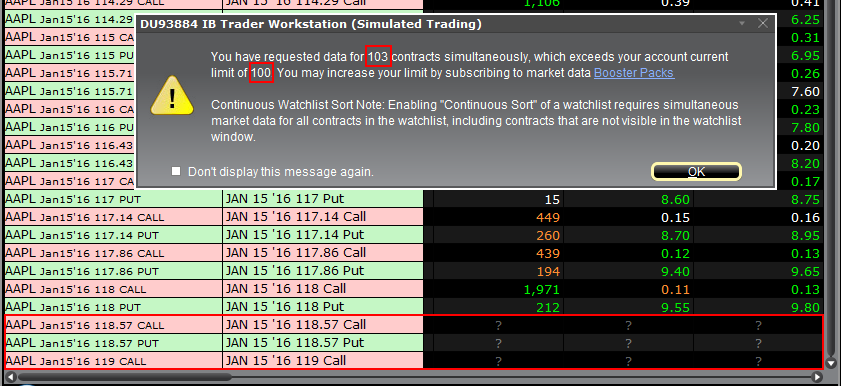
There are various functions and tools in TWS using market data: watchlists, charts, trading or analytical tools, alarms. In general, any foreground window which actively uses market data for display or for calculations, will increase the total number of market data channels currently opened. Once you have exceeded the maximum Market Data allowance for your account, you will be prevented from receiving additional market data. In this case, one or more tickers will show a "?" instead of actual quotes and your TWS will display the following warning message:
"You have requested data for XXX contracts simultaneously, which exceeds your account current limit of YYY. You may increase your limit by subscribing to market data Booster Packs."
Note: If you have decided to hide the warning by ticking the checkbox "Don't display this message again", you will not see it again next times you exceed the market data limit. Nevertheless you will still see "?" for one or more tickers instead of the actual quotes.
Where can I check the current market data allowance?
Within TWS, you can check how much of your total market data allowance you are currently consuming in the "Maximum Allowed" window. While in TWS, press the keys Ctrl + Alt + = (on a MAC click: Control + Option + =) and you will see the Maximum allowed pop-up indicating the market data allowance (the value close to "Simultaneous TWS market data subscriptions") and the market data lines currently used (the value close to "Currently subscribed top market data count".)
Which solutions are available to me?
-
Reduce the number of financial instruments displayed within your trading platform
To overcome an excessive market data usage, the easiest solution is to reduce the amount of financial instruments present within your trading platform. Here below are some ways to accomplish that:
a. Delete some tickers from your watchlist(s). There might be old tickers you are no longer interested in or there may be expired contracts. Deleting those will reduce the overall market data usage.
b. Minimize or hide one or more watchlist or other tools consuming market data. Only the TWS windows which are active and in the foreground contribute to market data count. If you have floating watchlists/charts and you minimize them or send them to the background, you will actually decrease the overall market data usage by the number of tickers present on those watchlists/charts
c. Use more restrictive filters within Option Trader / Option Chains / Strategy Builder. Those tools often become top market data consumers due to the high number of option contracts they display. All those tools provide filtering based on strike / expiry / trading class. By acting on those filters you can reduce the number of option contracts displayed
Note: Some derivatives contracts (Futures, Options, Future Options) will often consume two market data channel, one for the contract himself and one for the underlying, since the underlying contract is used for Greeks / Volatility calculations
-
Purchase Quote Booster pack(s)
Each Quote Booster pack will cost you 30 USD monthly and will entitle you to 100 additional market data lines (on the top of your current allotment). The maximum number of Quote Booster packs you can purchase for your account is 10.
How to fix the "Cannot create ... file" error during TWS installation on MacOS
The filesystem permissions are controlled by your machines operating system. One of their functions is to secure your files, preventing unauthorized access or undesired modifications to the system and to your personal data.
Some software on your computer may modify or override the permissions assigned by the operating system. Under certain circumstances, this prevents the TWS installer from accessing the folder where the application core files have to be created (/users/youruser/home/Applications). In such cases, the TWS installation usually displays the error "Cannot create ... file. Shall I try again?"
Procedure:

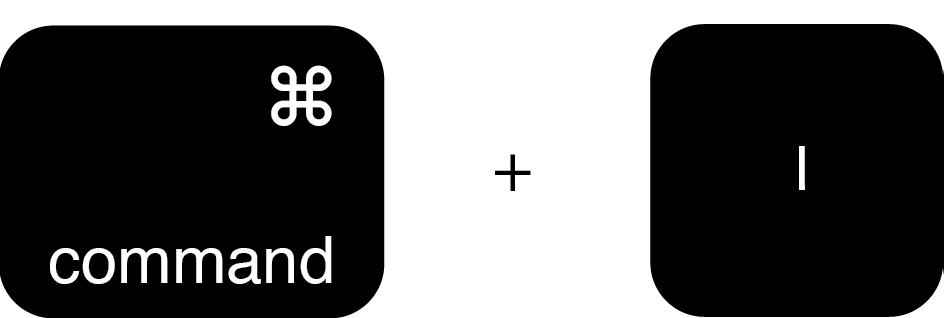
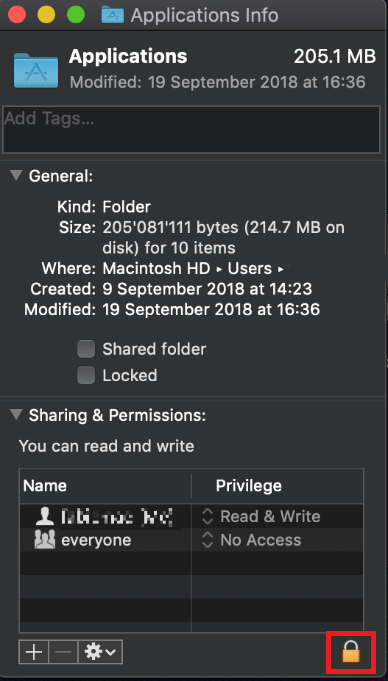
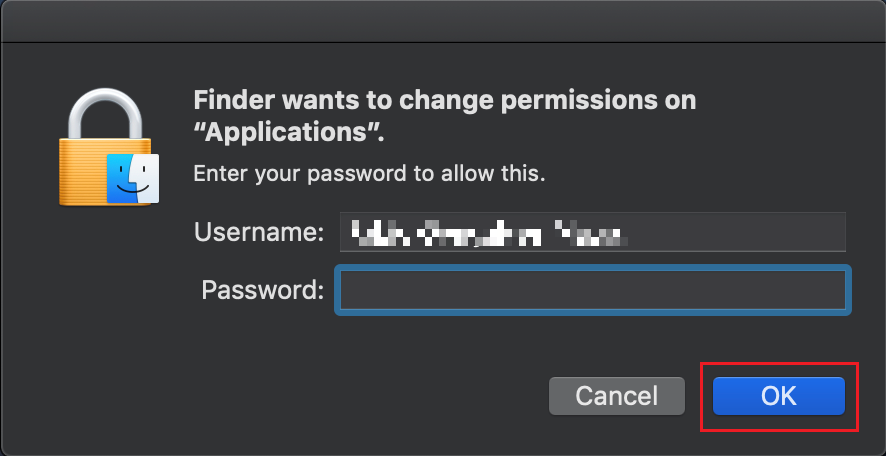
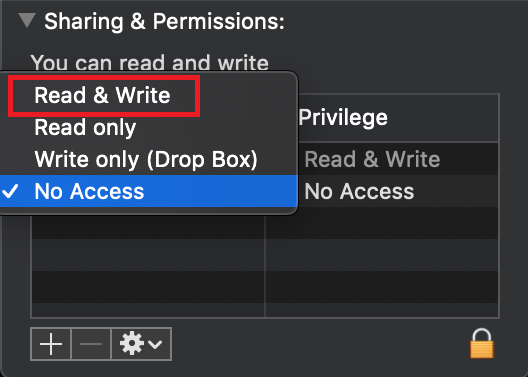
.png)
.png)
.png)
7. Once the installation has completed successfully, repeat the previous steps from 1. to 5. setting back the permissions of “everyone” to “Read Only” to revert your changes to the initial status
Complex Position Size
For complex, multi-leg options positions comprising two or more legs, TWS might not track all changes to this position, e.g. a vertical spread where the short leg is assigned and the user re-writes the same leg the next day, or if the user creates a the position over multiple trades, or if the order is not filled as a native combination at the exchange.
Fusión de IB TWS y IB Key en IBKR Mobile
RESUMEN
La migración para su usuario depende del uso actual de las aplicaciones:
1. Su teléfono inteligente solo se utiliza para negociar (IB TWS instalada) - Haga clic aquí
2. Su teléfono inteligente solo se utiliza para autenticación (IB Key instalada) - Haga clic aquí
3. Su teléfono inteligente se utiliza para negociación y autenticación (IB TWS y IB Key instaladas) - Haga clic aquí
4. Su teléfono inteligente se utiliza para transacciones de tarjeta de débito (IB Key instalada) - Haga clic aquí
Usted es usuario de IB TWS
Ha negociado desde su teléfono inteligente con la IB TWS y no ha utilizado la IB Key.
1. Tras el primer uso de la aplicación, verá la siguiente pantalla de Inicio.
La Figura 1 es la pantalla de Inicio de IBKR Mobile para dispositivos iOS. La Figura 2 es la versión para dispositivos Android.
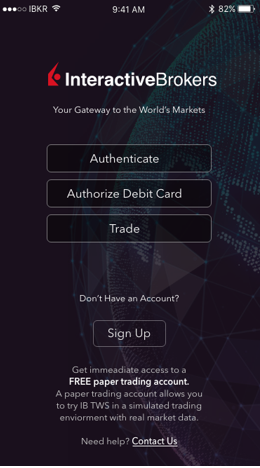
Figura 1 Figura 2
2. Pulse en el botón Negociación (Trade).
3. El resto de la experiencia de la aplicación es idéntico a lo que ya ha utilizado en el pasado.
Acceso a las otras funciones desde la pantalla de negociación
Si desea acceder a las otras funciones de IBKR Mobile, como el módulo de Autenticación o
funciones de tarjeta de débito:
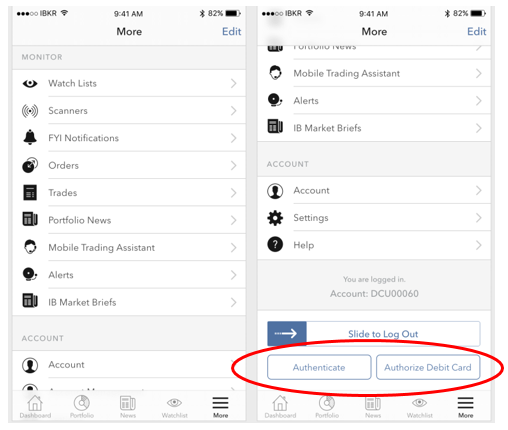
Para iOS (Figura 3)
1. Abra el menú ‘Más’ (esquina inferior derecha de la pantalla).
2. Baje al fondo de esta pantalla
Para Android (Figura 4)
1. Abra el menú de la aplicación
2. Baje a la sección inferior: ajustes de aplicación
.png)
Figura 3 Figura 4
Usted es usuario de IB Key
Activación
1. Lance la IBKR Mobile y pulse en Autenticación.
2. La aplicación detectará la instalación de la IB Key y sugerirá un curso de acción; o bien una
migración automática (Figura 5) o bien una actualización y después una migración automática.
También puede elegir hacer la migración de forma manual en otro momento.
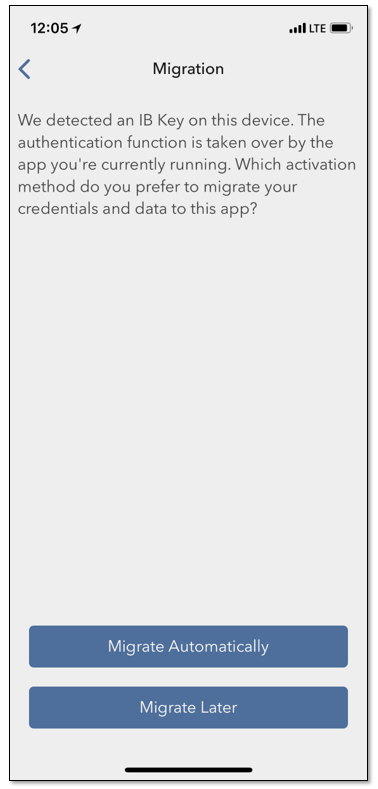
Figura 5 Figura 6 Figura 7
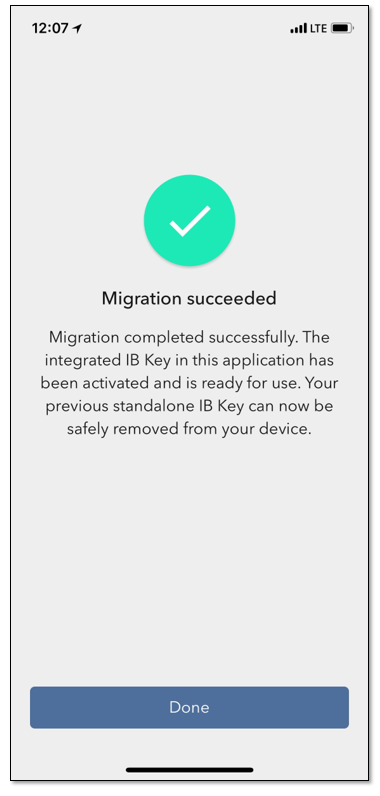
Una vez completada la migración, si ejecuta la aplicación IB Key independiente, con la que se ha
autenticado en el pasado, verá la siguiente pantalla (Figura 8).
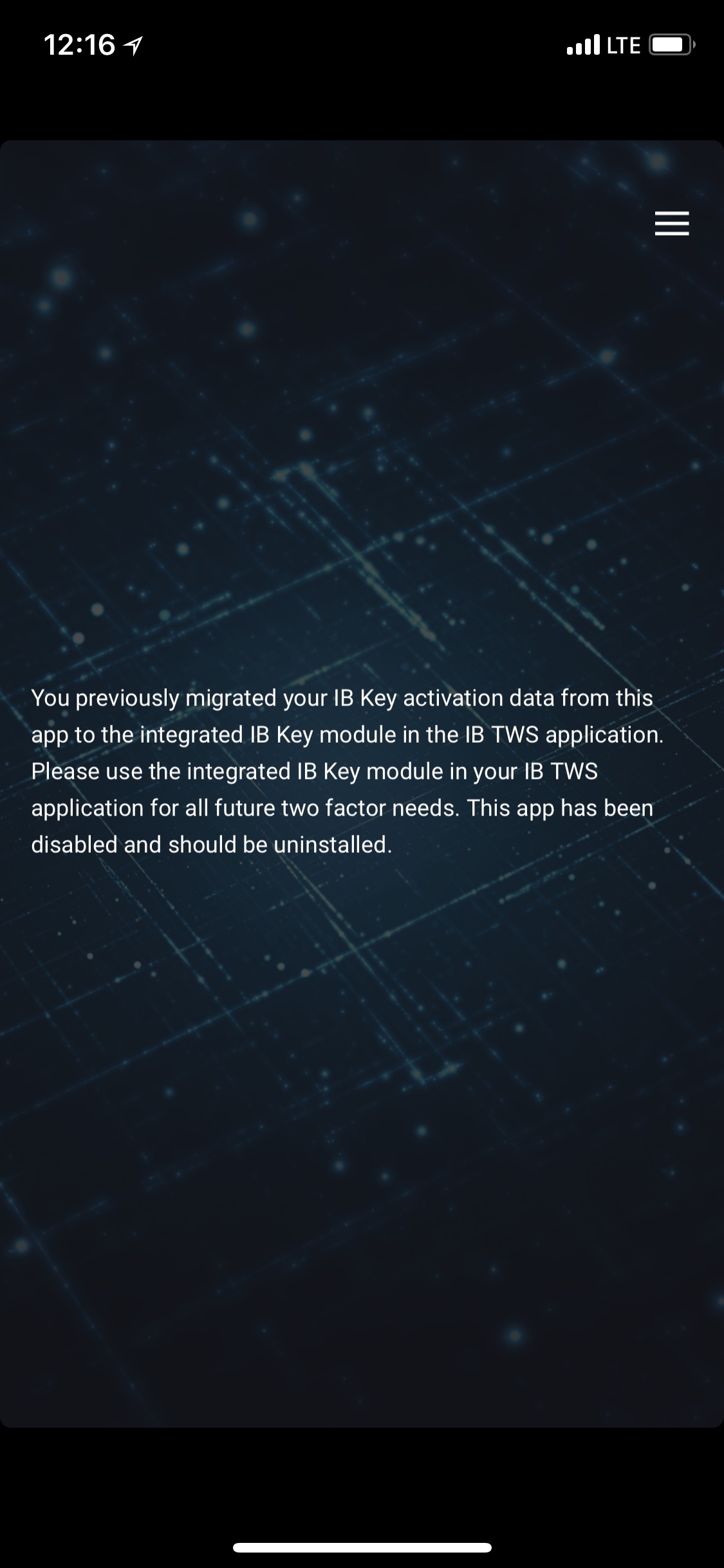
Figura 8
Operación diaria
A. Nada cambia en la experiencia diaria de conexión si usted tiene conexión a Internet - se utilizará
el proceso de autenticación ininterrumpida:
1. Introduzca sus credenciales en los campos correspondientes (en TWS, Gestión de Cuenta, WebTrader o
IBKR Mobile). Haga clic en Conexión (Login).
2. El sistema le enviará una notificación a la pantalla de su teléfono; púlsela.
3. Según su dispositivo, presente su cara a la cámara o la huella en el sensor (iOS) o
introduzca su código PIN (Android). El sistema procederá automáticamente con la conexión.
B. Si no tiene conexión a Internet, utilizará el IBKR Mobile en modo desafío-respuesta:
1. Introduzca sus credenciales en los campos correspondientes (en TWS, Gestión de Cuenta, WebTrader o
IBKR Mobile). Haga clic en ‘Conexión (Login)'.
2. Haga clic en el enlace que indica “No he recibido una notificación”.
3. Lance la IBKR Mobile y pulse en ‘Autenticación’.
4. En el campo Desafío de su aplicación del teléfono inteligente introduzca los valores que se muestren en la pantalla de Conexión. Pulse el botón ‘Generar’.
5. Introduzca los valores mostrados por su teléfono inteligente en el campo Cadena de respuesta en la Conexión. Haga clic en ‘Conexión’.
Usted es usuario tanto de la IB TWS como de la IB Key
1. Por favor, complete primero el procedimiento para la activación del módulo de Autenticación de la aplicación móvil IBKR (Haga clic aquí).
2. Conéctese a la pantalla de negociación pulsando en el botón Negociación (Trade) en la pantalla Inicio en su nueva aplicación móvil IBKR (Haga clic aquí).
Usted utiliza una tarjeta de débito IB
1. Por favor, complete primero el procedimiento para la activación del módulo de Autenticación de la aplicación móvil IBKR (Haga clic aquí).
2. En la pantalla de Inicio de la IBKR Mobile pulse en el botón Tarjeta de débito. El resto de la experiencia
es idéntico a lo que ya ha utilizado en el pasado.
How to overcome the "Downloading settings from server failed" error
Store settings on server allows clients the ability to store their Trader Workstation (TWS) settings/configuration on the cloud and retrieve them at anytime from another computer. This feature allows you to use the layout of a specific user on two or more machines.
In some specific circumstances, the operation which stores/downloads the settings to/from the cloud may fail and the following error message may appear shortly after the TWS has loaded on the screen:
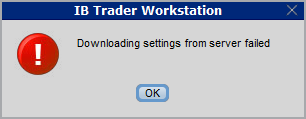
How to overcome this error message?
The underlying causes of this message are usually the following:
- ACCESS TO THE LOCAL MACHINE IS BLOCKED: A security setup, such as a firewall or antivirus, prevents the access of this computer to the cloud storage. This prevents TWS from accessing the remote server, thus disallowing the settings file upload or download. Recommended workaround: set up an exception on the firewall or antivirus in order to exclude the TWS executable file (c:\Jts\tws.exe) or the entire TWS folder (C:\Jts) from the real time security scan. The procedure to set an exclusion may vary, according to the software you are using, therefore we recommend consulting the user guide or the on-line documentation of your specific security program.
- ACCESS TO THE REMOTE SERVER IS BLOCKED: A firewall or proxy service blocks the communication with the cloud storage through the network on which this computer is. In this scenario, you (or your IT / Networking departments, in case you do not have the rights for such an operation) can modify the firewall or proxy settings to allow the computer to communicate with the cloud server s3.amazonaws.com on the TCP port 443. For additional details about the hosts/ports which needs to be allowed for the proper TWS operation, please see as well the section "DESKTOP TWS" of KB2816. Please refer to the documentation of your specific software in order to create specific rules for your firewall or proxy system.