如何在盘前或盘后时段交易股票?
默认情况下,一些产品在下单时会自动带有一项名为仅限常规交易时间(RTH)的限制。 这一限制会阻止委托单在盘前和盘后时段成交。本文详细阐述了这一时间限制并就如何修改限制进行了说明。
在常规交易时间(RTH)以外交易存在流动性降低,波动率上升和错误交易指引增多等固有风险,在此期间将活跃委托单传入市场之前,交易者应充分注意并做好准备承担相关风险。
目录:
如何确定提交的委托单是否有常规交易时间限制。
更改默认设置
其它重要注意事项
如何确定提交的委托单是否有常规交易时间限制。
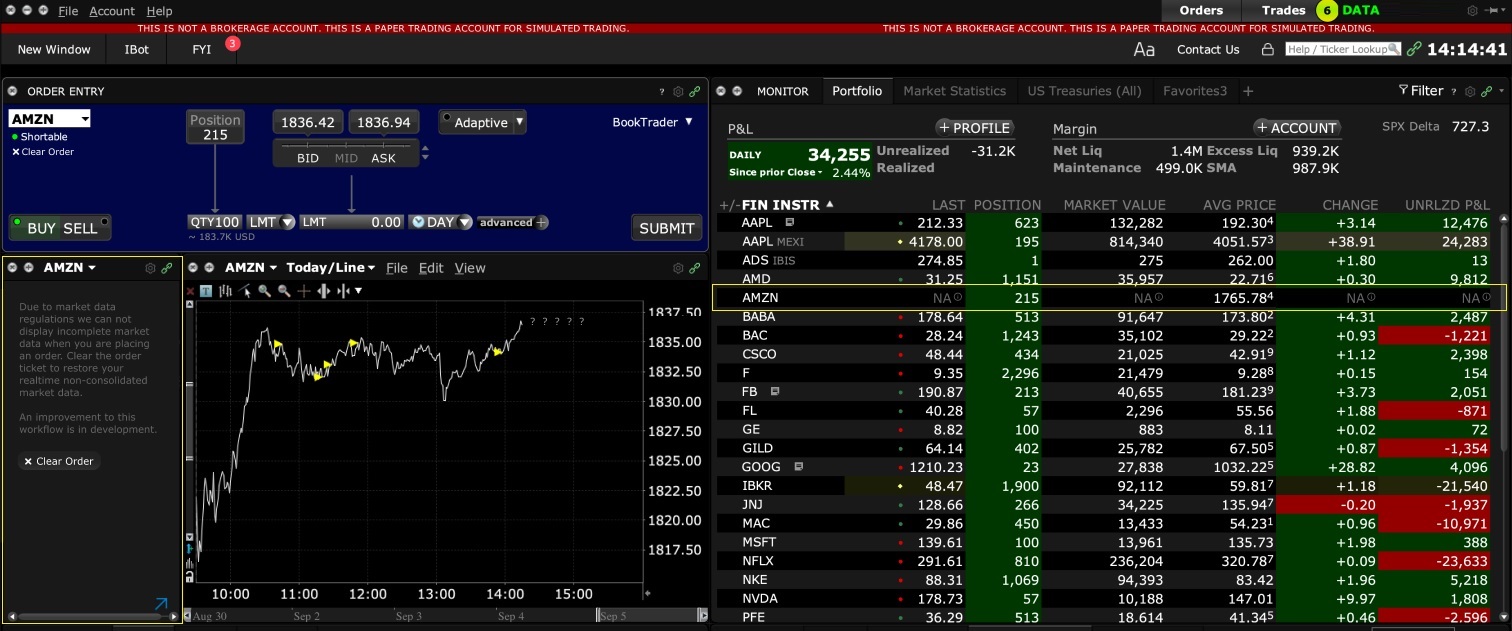
交易者工作站(TWS)
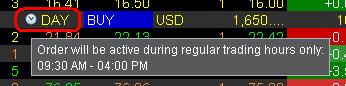
仅限常规交易时间成交的委托单其生效时间(TIF)的位置会有一个时钟图标。
将鼠标停留在时钟图标上会显示委托单何时可以成交的相关信息。
没有时间限制的委托单或者不会有时钟图标,或者出现的时钟图标上会带有一个感叹号,表示委托单会在常规交易时间以外保持工作状态。
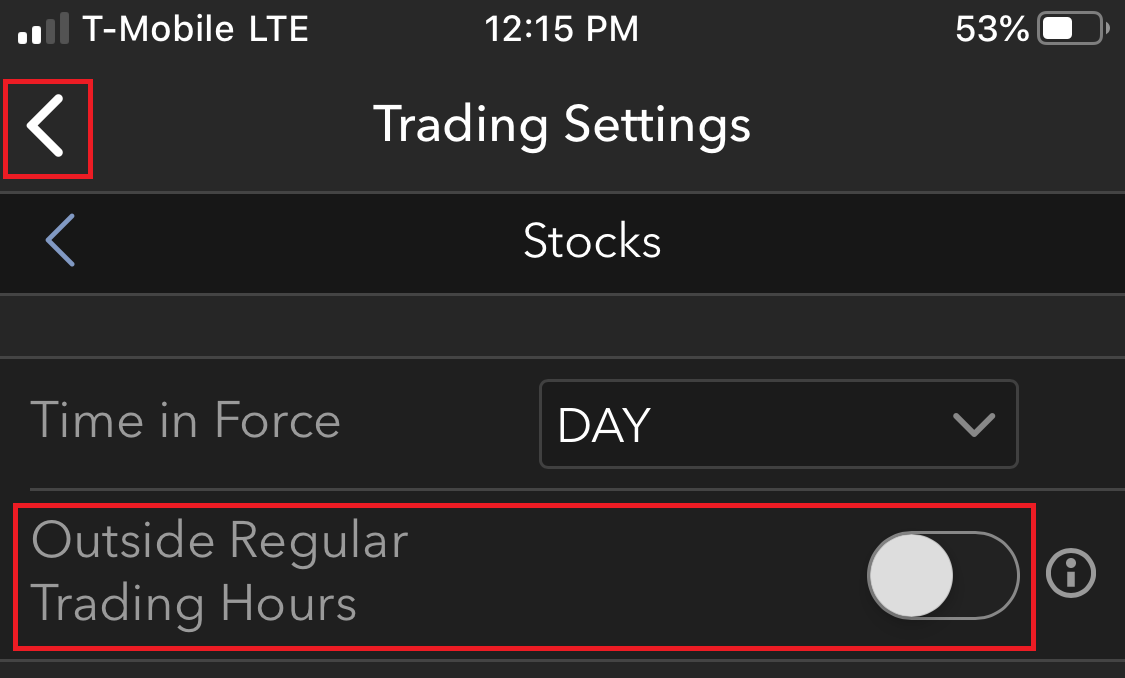
交易者可在委托单传递之前点击该位置更改常规交易时间设置。 点击后,从下拉菜单中选择“常规交易时间以外成交”。
移动IBKR
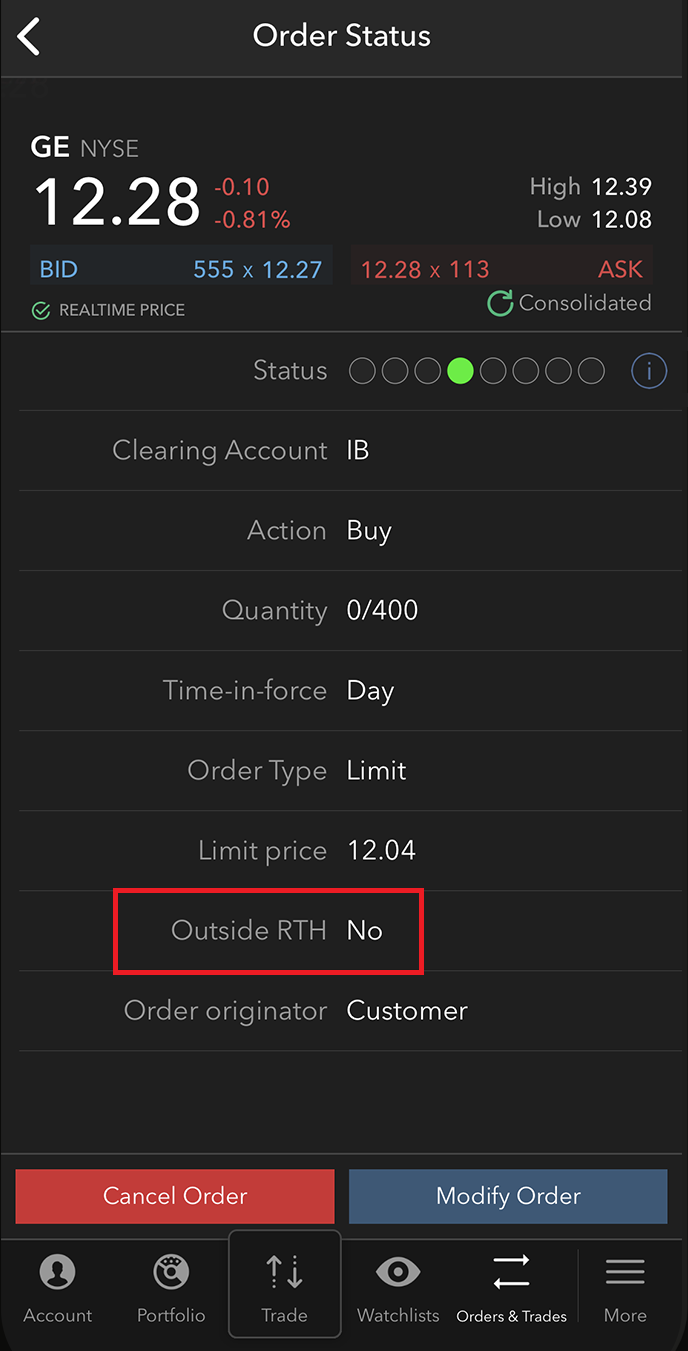
要查看自己的委托单是否可以在常规交易时间以外成交,请打开“委托单与交易”标签页(iOS)或“委托单”标签页(安卓)点击对应委托单。如果使用的是iOS应用程序,会有一行直接显示委托单是否可以在常规交易时间以外成交:
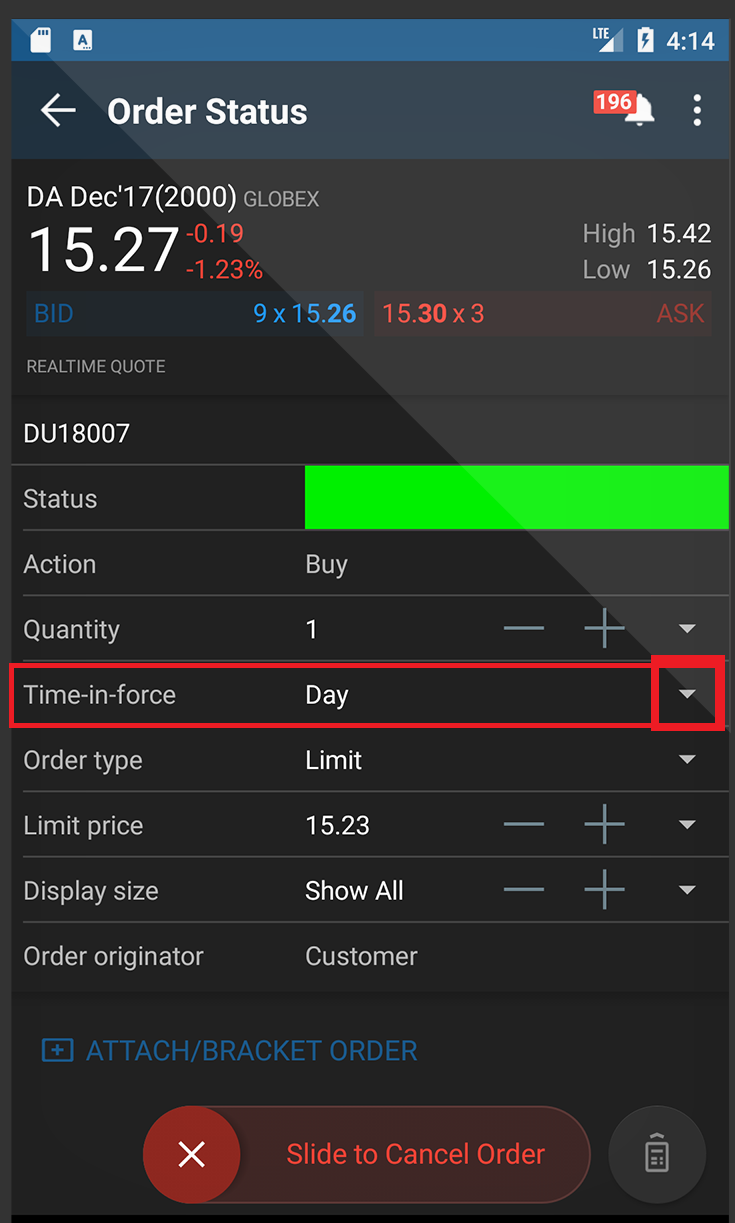
如果使用的是安卓应用程序,您会看到“生效时间”。点击“生效时间”右侧的小箭头展开。会有一个名为“常规交易时间以外”的切换键为开启(可以在常规交易时间以外成交)或关闭(不能在常规交易时间以外成交)状态。
客户可以通过移动IBKR的委托单指令单(Order Ticket)设置委托单在常规交易时间以外成交。无论是iOS版移动IBKR还是安卓版移动IBKR,委托单指令单上都有一行可供您开启或关闭常规交易时间以外成交功能。选好后,再将指令单填写完整就可以提交了。
iOS:
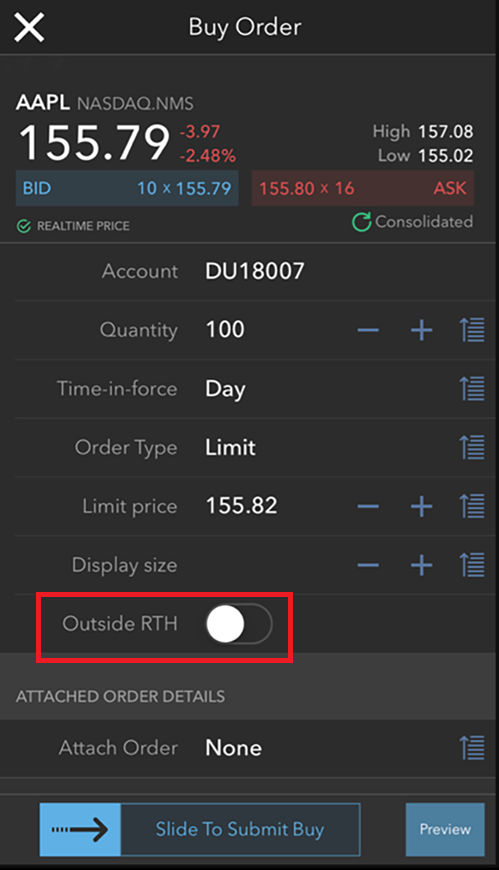
安卓:
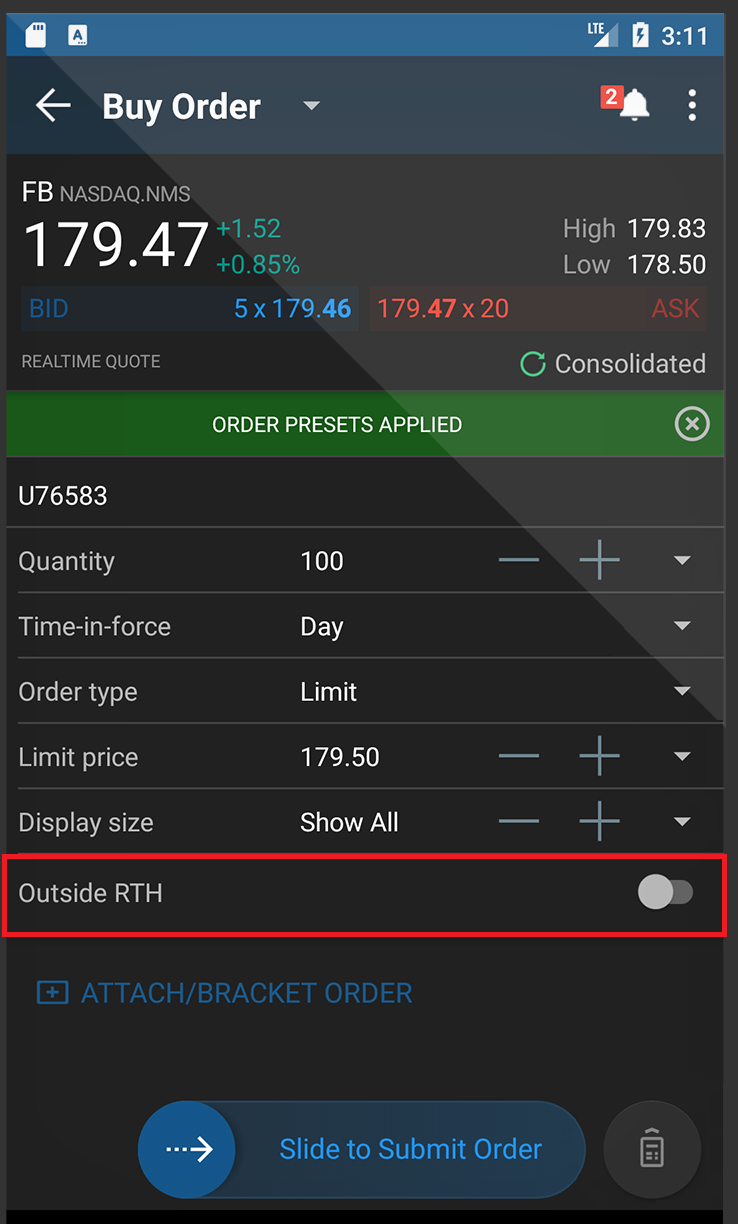
注意:委托单一经传递,常规交易时间限制便不能修改。 要更改常规交易时间限制,必须将已提交的委托单取消,再选择想要的常规交易时间设置重新下达委托单。
更改默认设置
交易者工作站(TWS)
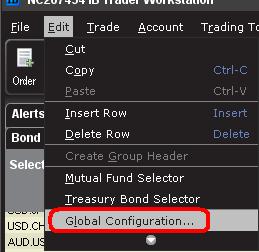
交易者可在TWS中更改默认的常规交易时间设置,方法如下:
1. 在TWS主界面顶部选择“编辑”菜单,再选择“全局配置”。
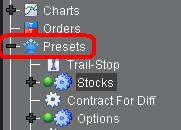
2. 在出现的窗口左侧点击预设旁边的“+”号展开。
2. 点击文字选择产品类型(股票、期货等),选中的文字会突出显示。
3. 在主委托单部分,确保委托单类型设置为限价单(LMT)。(如果是市价单或止损单,则无法应用常规交易时间设置)。
4. 在定时部分勾选复选框“允许委托单在常规交易时间以外激活、触发或成交”。
5. 在窗口底部点击“应用”,然后再点击“确认”。
6. 支持更改常规交易时间限制的委托单(第1步中选择的产品)将采用新的默认设置创建。
移动IBKR
交易者可在移动IBKR(iOS或安卓)中更改默认的常规交易时间设置,方法如下:
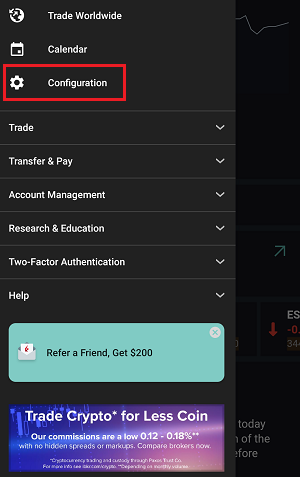
- 点击菜单(“更多”)按钮,选择“配置”
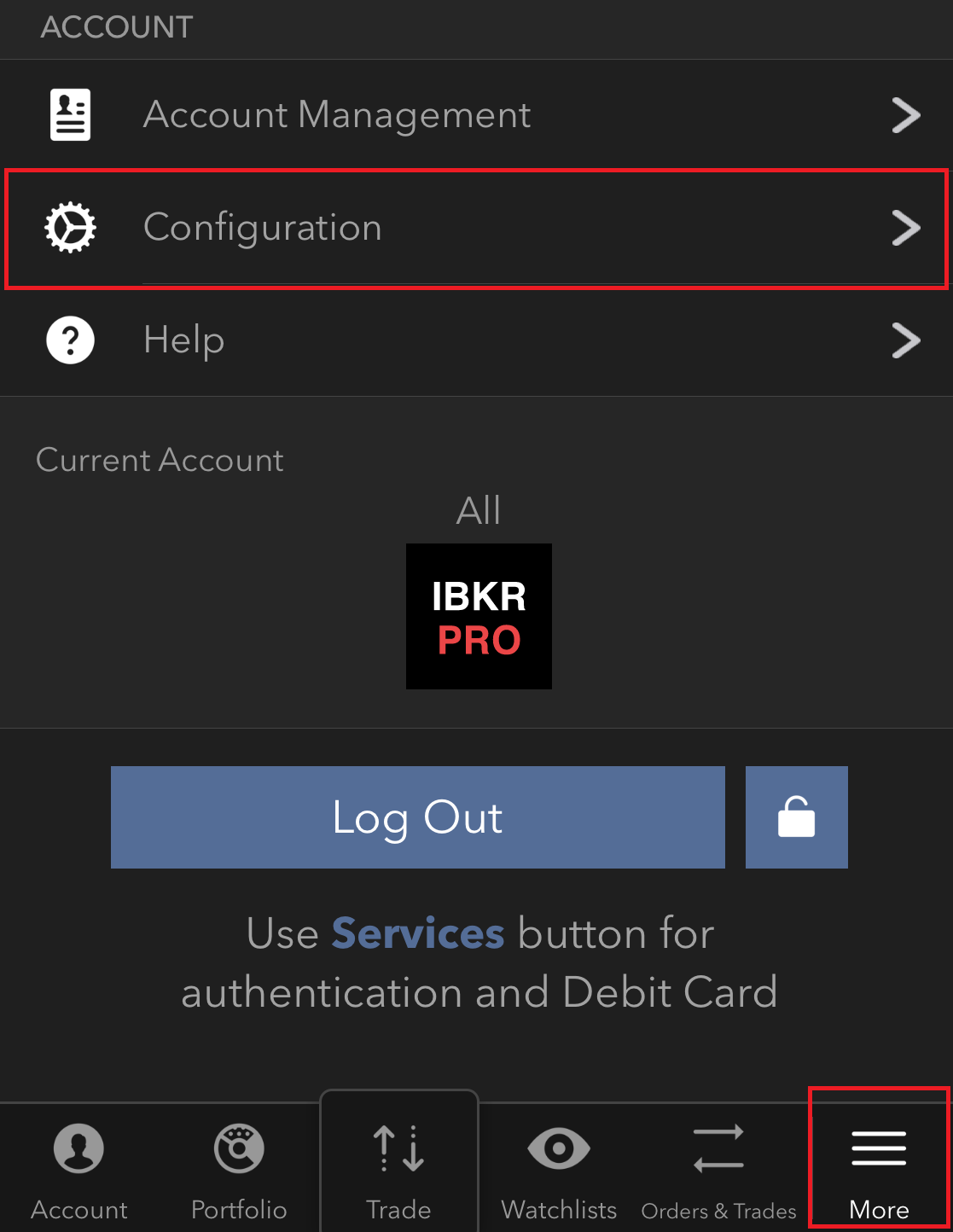
- 找到“云端”部分,点击“交易设置”
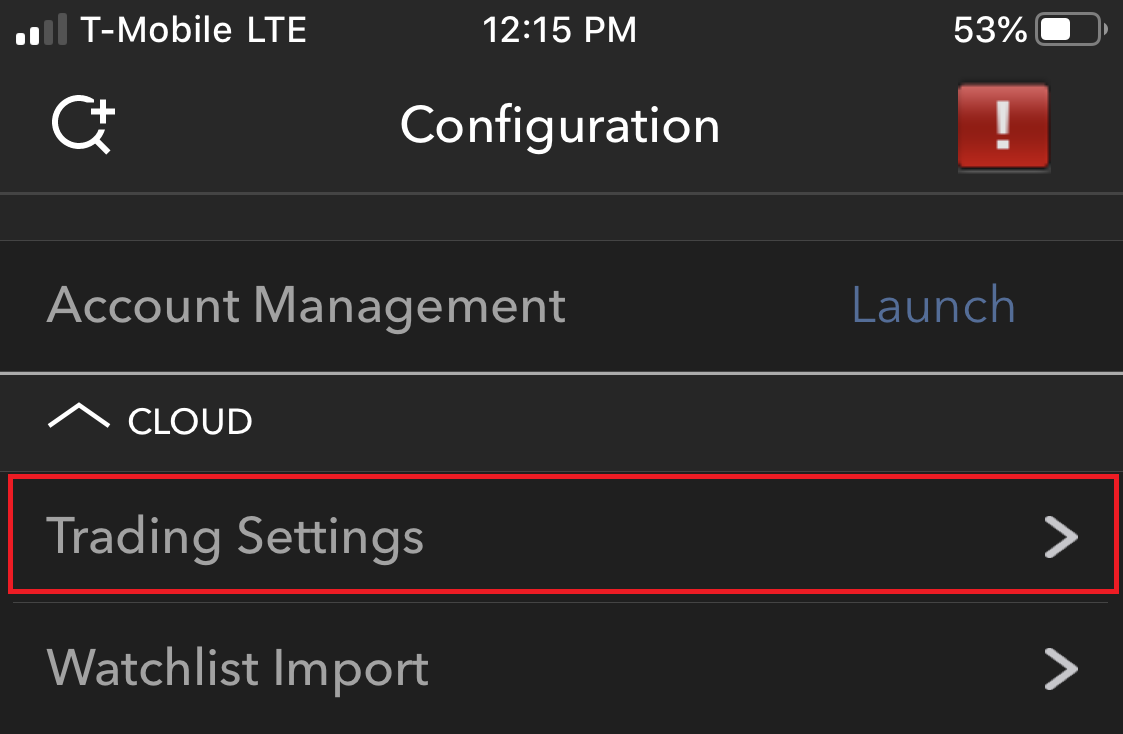
- 点击您想更改预设的产品
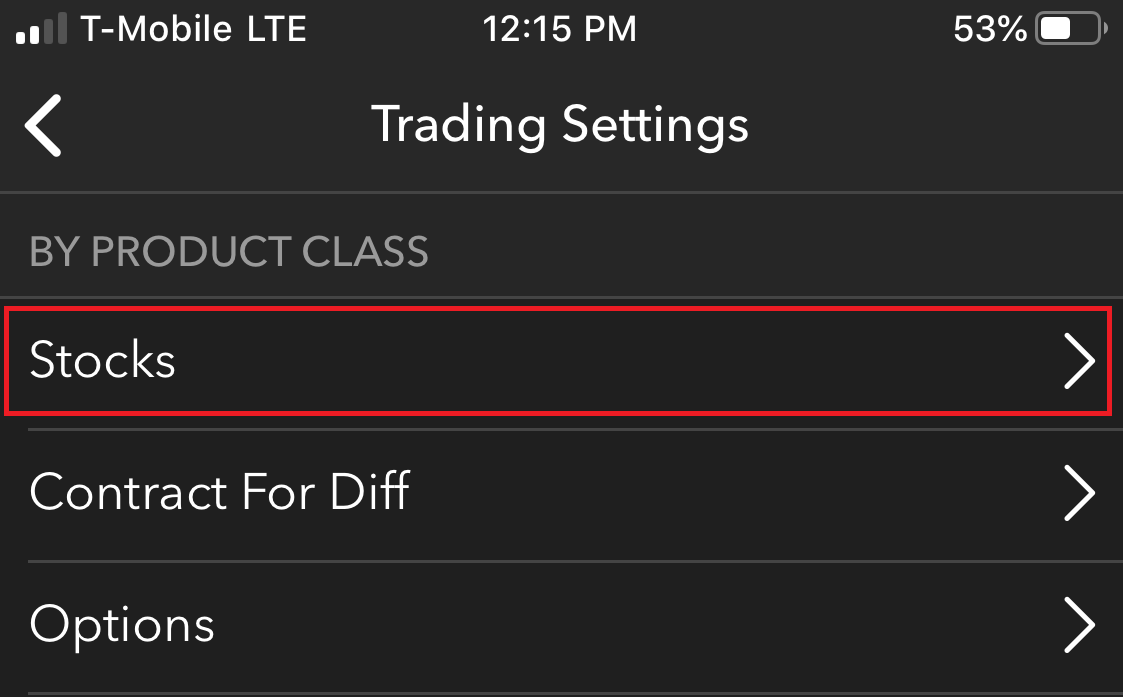
- 点击“定时”
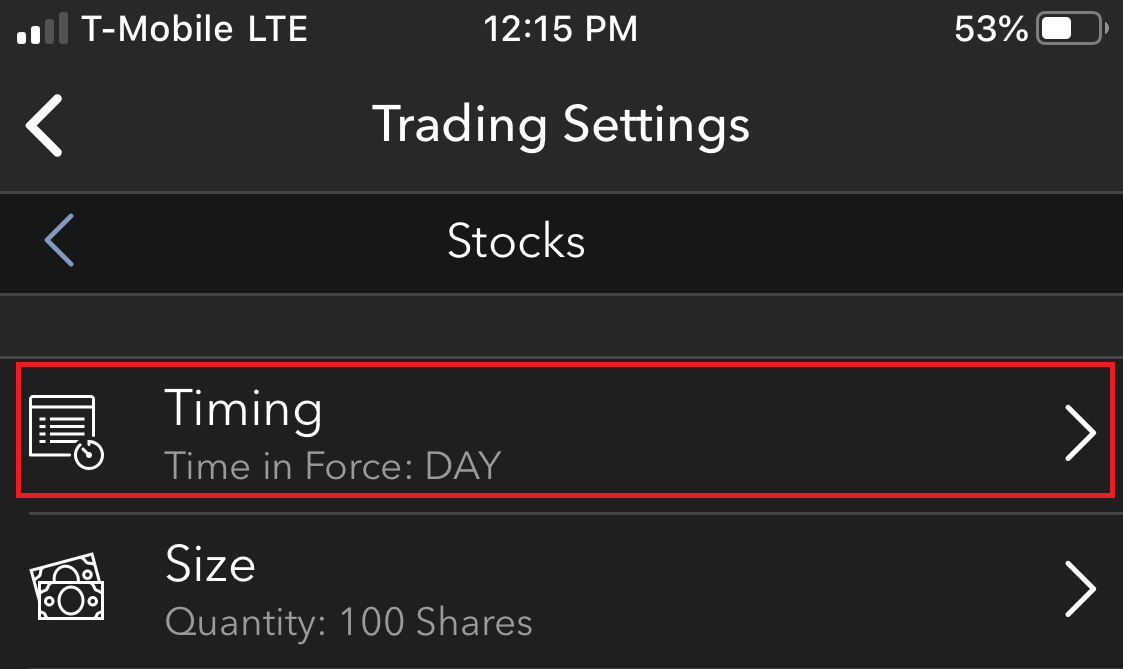
- 开启或关闭常规交易时间以外成交功能。完成后,只需点击返回按钮将您的更改保存至云端即可。
其它重要注意事项:
* 不清楚某一特定产品常规交易时间的交易者可右键点击市场数据行,选择“合约信息”>“描述”。 该窗口会显示对应产品的常规交易时间。
* 外汇、OTCBB和粉单市场证券由于没有集中的市场或主交易所,因而没有指定常规交易时间。 如果在交易时段刚开始或快要结束时交易该等产品,交易者应保持谨慎,因为这种情况下无论默认的常规交易时间限制如何,委托单都会执行。
* IBKR Pro版账户的常规交易时间以外时段自美东时间4:00点开始,一直持续到开市,并自收市开始持续到美东时间20:00点。 IBKR Lite版账户的常规交易时间以外时段自美东时间7:00点开始,一直持续到开市,并自收市开始持续到美东时间20:00点。两种账户类型的常规交易时间都是美东时间9:30-16:00。
* 就股票而言,市价单和(触发后会成为市价单的)止损单都只会在美东时间09:30至16:00(即纽交所的常规交易时间)保持活跃生效。要使委托单在所有时段(包括盘前时段、常规交易时段和盘后时段)都保持活跃生效,您必须使用限价单或止损限价单并将委托单属性设置为“允许在常规交易时间以外成交”。同样的设置也适用于CME/CBOT/NYMEX/COMEX期货合约。纽约期货交易所(NYBOT)会接受止损单并在内部将其转换成在所有时段都活跃生效的“有保护的止损单”。期货合约的常规交易时间请参见合约描述。
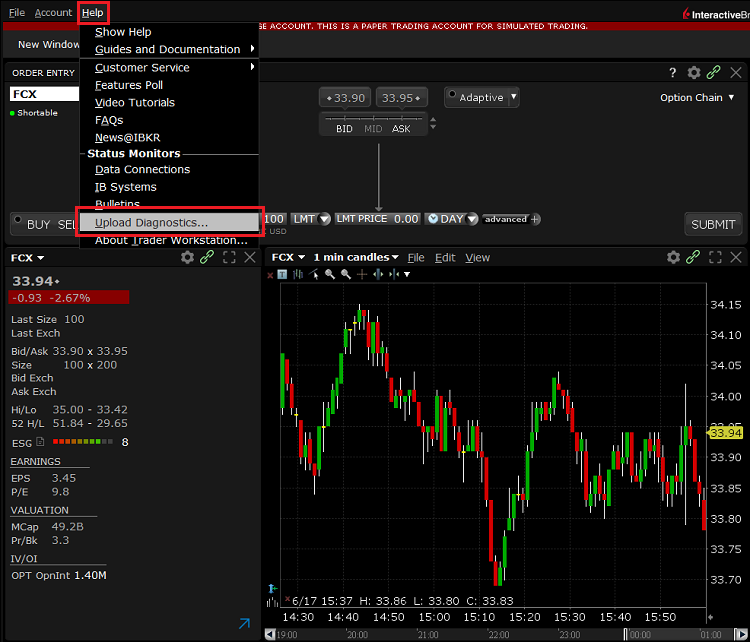
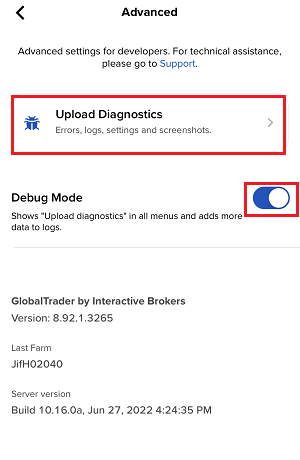
如何从IBKR平台上传诊断包
某些支持相关的问题除了需要提供截图外还需要上传诊断文件与日志。这些信息可帮助我们调查并解决您遇到的问题。
本文详细说明了如何通各盈透证券交易平台上传诊断文件与日志。
请注意:IBKR不会实时监控诊断包信息库。如果您在没有盈透证券明确要求的情况下自行决定上传诊断包,请通过咨询单或电话通知我们的客户服务人员,否则我们可能会注意不到您的错误报告。
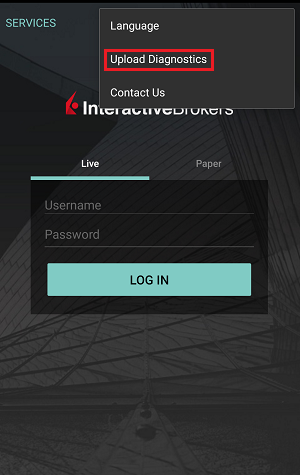
请根据您使用的平台点击对应链接:
-
移动IBKR(Android版)
-
移动IBKR(iOS版)
- Windows和Linux操作系统:按Ctrl+Alt+Q
- Mac:按Cmd+Option+H
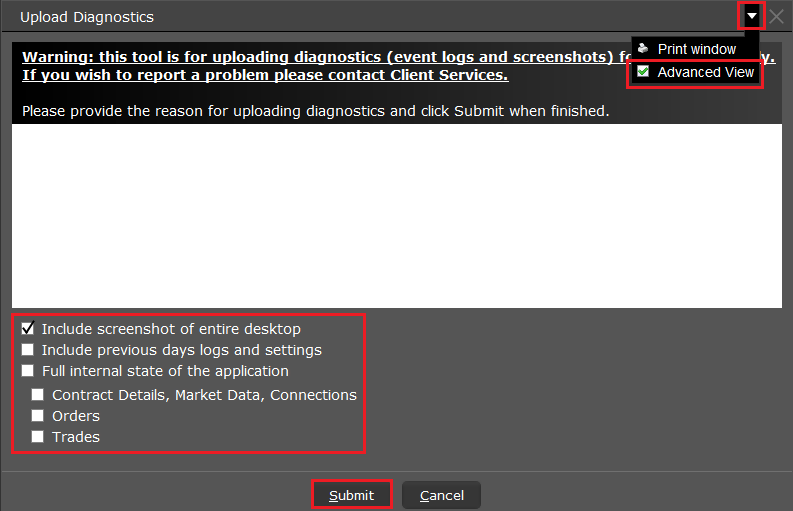
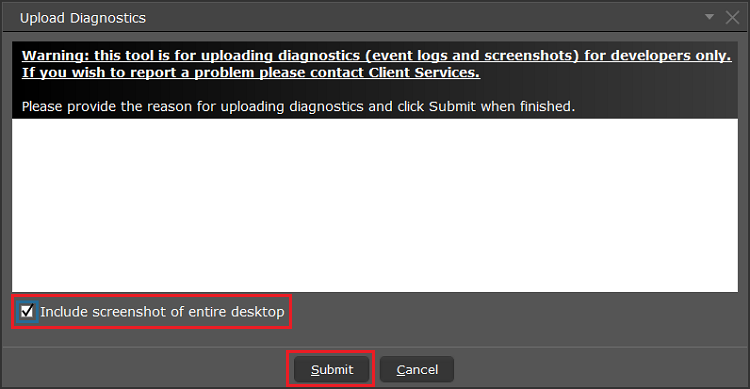
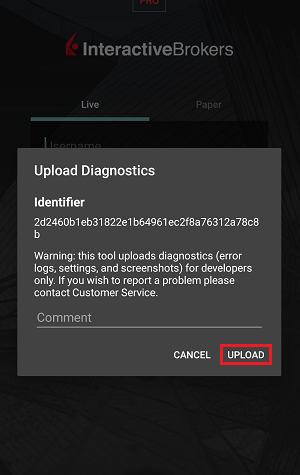
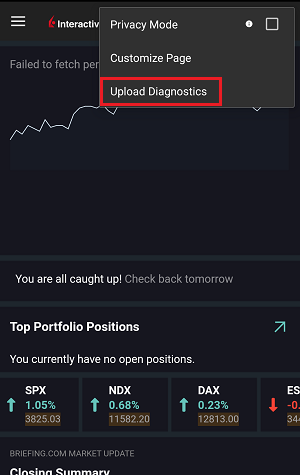
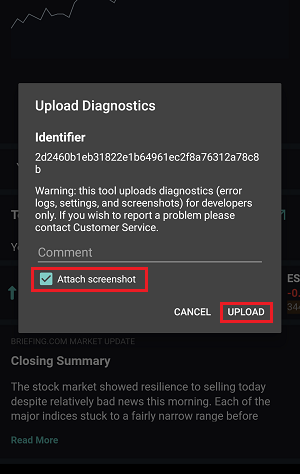

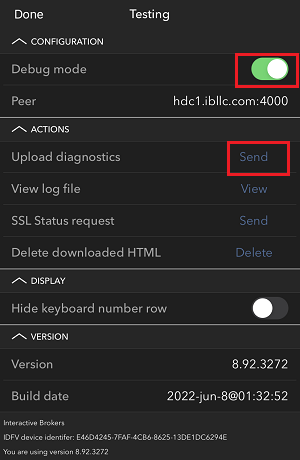
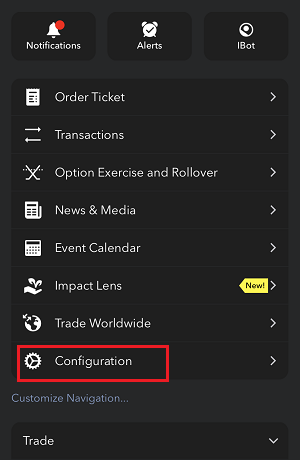
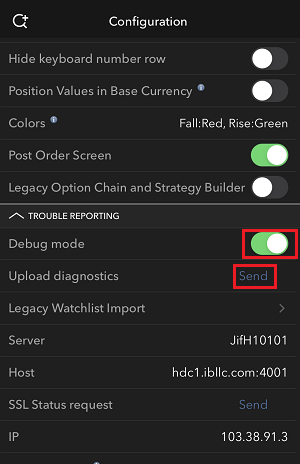
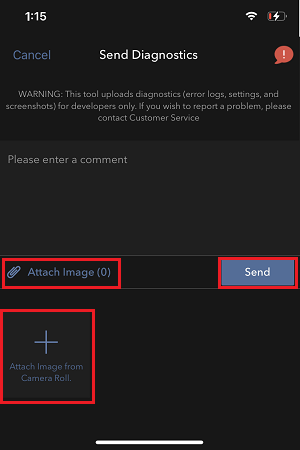
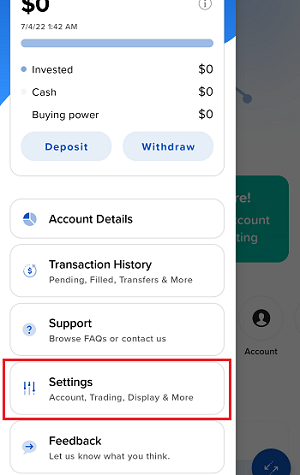
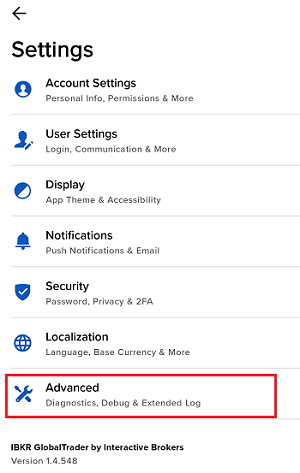
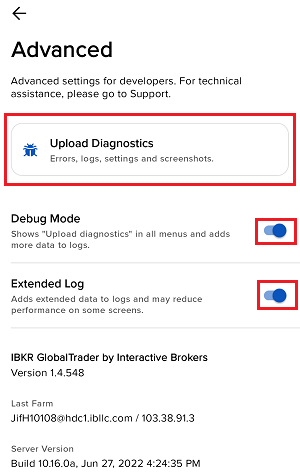
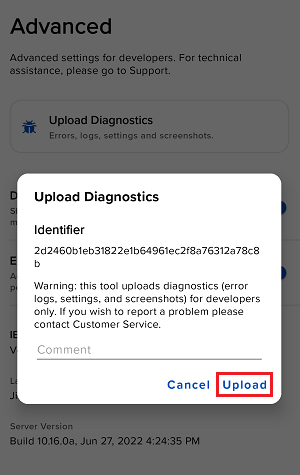
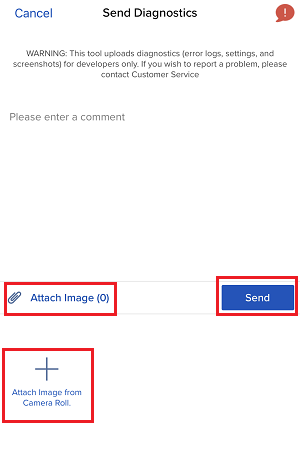
7. 输入您的评论,点击“附上图片”按钮附上您已保存到相册的问题页面截图
客户端的诊断上传请参见IBKB3512
TWS安装和更新过程中可能出现的警报
IBKR的交易者工作站(TWS)是一个全球交易系统,可供客户使用一整套在线交易工具。TWS可以安装于Windows、Mac OS X和Linux系统,需要Java运行时环境(JRE)。因此,在安装TWS时,同时还会下载必要的Java文件以使用Java虚拟机(JVM)运行。
有时在TWS的安装或更新过程中,诸如杀毒软件之类的应用程序会弹出警报并阻止安装或更新程序完成。这种情况下出现的警告和其它消息可以忽略,您可以继续完成交易平台的安装。
目录
ibkr.com或IBKR地区网站上下载页面的TWS安装程序均采用行业标准要求的所有安全程序进行数字签名和封存,没有任何恶意代码或程序。TWS更新包也是采用同样的行业标准,启动TWS时,会自动下载安装更新包(当且仅当有更新的时候)。但是,如果您收到警报,我们还是建议您谨慎对待。如果您想将TWS安装文件保留在电脑上以备将来使用,您应确保对其应用同样的预防措施,保护数据免受病毒和恶意软件攻击。
您可能会看到一条警报(类似于图1但不限于图1的情况),然后您的安全系统会等您来告诉它如何处理可疑文件。通常您可以选择隔离文件、删除文件、忽略文件或为该文件创建一个例外。
请注意,您的杀毒软件可能会自动隔离或删除TWS安装文件或其部分组件,而不会先请求您的确认也不会显示任何警告。但是,这只有在您对杀毒软件进行了特定设置让其作出这种反应的情况下才会发生。
图1
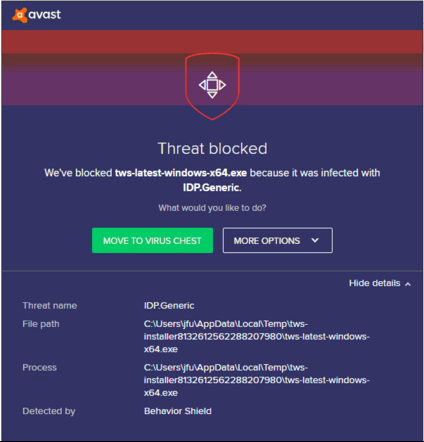
如果在TWS安装或更新过程中收到警告,我们建议您按以下步骤操作:
1. 删除TWS安装程序并重新从IBKR主网站或地区网站上下载
a) 删除您电脑上已有的TWS安装文件,然后再从回收站将其删除(清空回收站)
b) 在下表中点击与您所在地区对应的TWS下载区域
| 所在地 | TWS下载区域 |
| 美国 | https://www.ibkr.com |
| 亚洲/大洋洲 | https://www.interactivebrokers.com.hk |
| 印度 | https://www.interactivebrokers.co.in |
| 欧洲 | https://www.interactivebrokers.co.uk https://www.interactivebrokers.eu |
c) 检查网站证书。如果网站证书失效、受损或过期,大多数浏览器会立即向您发出警报。但是,如果您想手动检查网站证书的有效性,请点击地址(URL)旁边的安全锁,确保连接显示为安全并且没有出现任何安全警告(见下方图2)。
图2
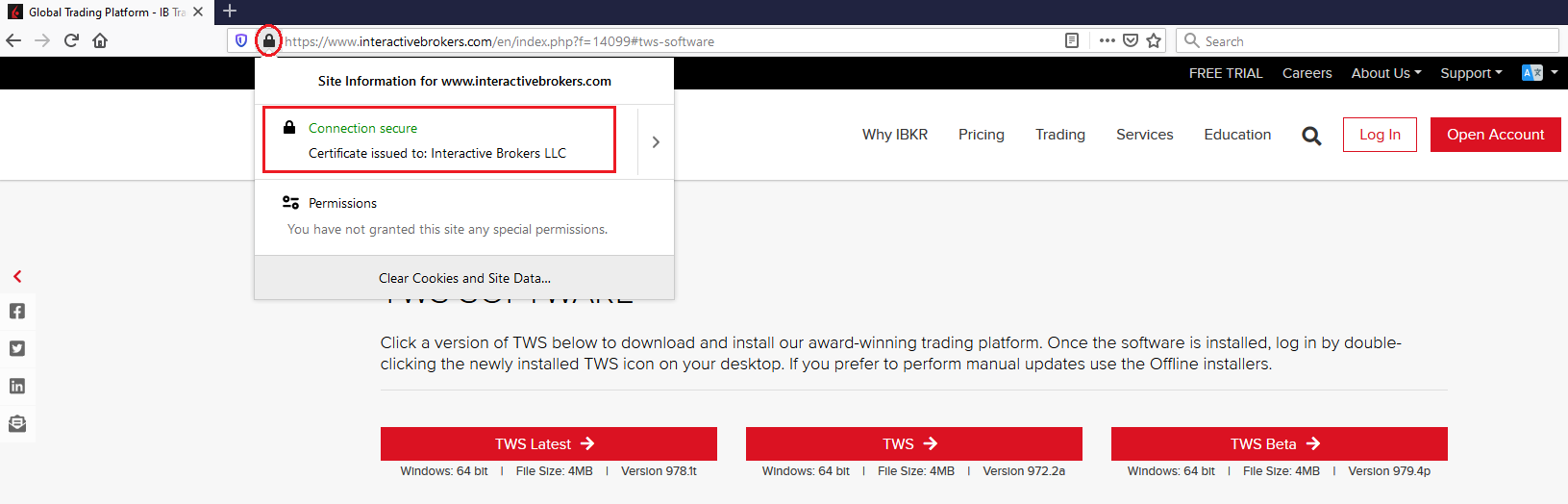
d) 点击您想要使用的TWS版本对应的按钮,再次下载TWS安装程序
2. 检查您所下载的TWS安装文件的数字签名
通常如果文件的数字签名有问题,您会立即收到安全警告。但是,如果您想手动检查,请根据您的操作系统按以下步骤操作:
Windows
a) 从Windows文件资源管理器打开下载(Downloads)文件夹或您保存TWS安装程序的文件夹
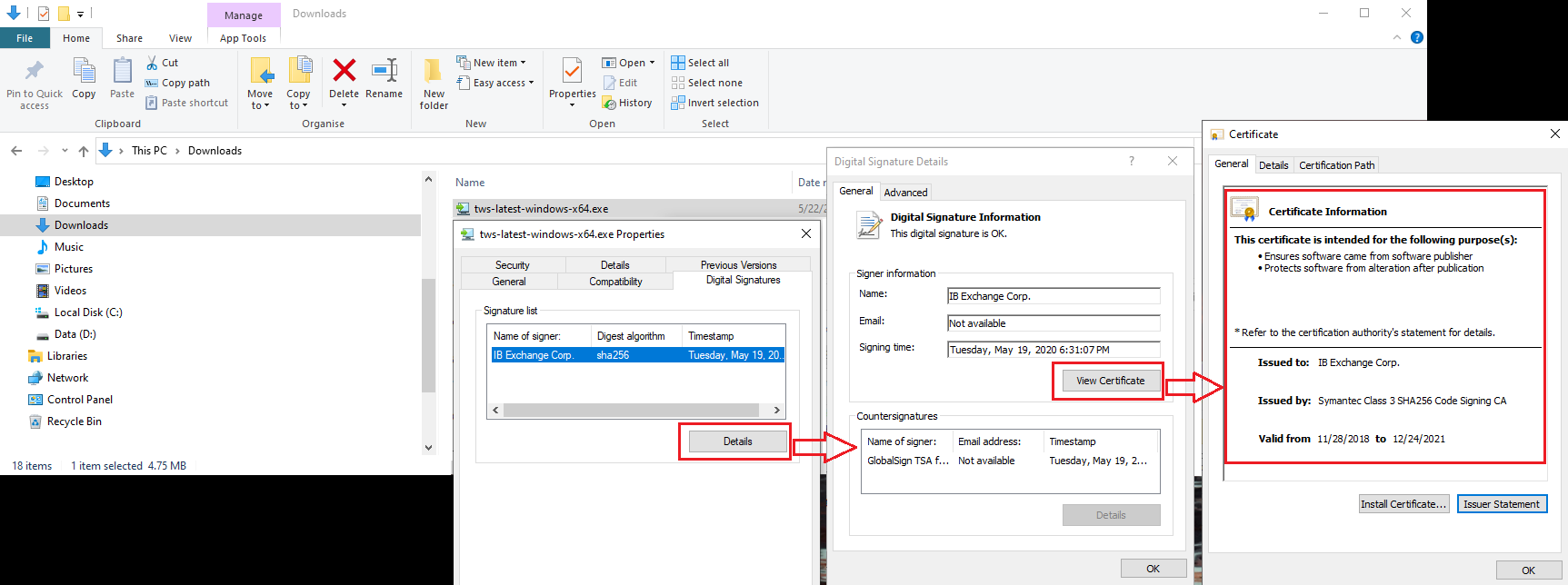
b) 右键点击TWS安装文件,选择属性(Properties)然后点击“数字签名(Digital Signatures)”
c) 点击“详细信息(Details)”然后点击“查看证书(View Certificate)”检查证书状态和签署者。合法的签署者为“IB Exchange Corp.”(见下方图3)
图3
Mac OS X
a) 点击屏幕右上角的放大镜(Spotlight搜索)然后输入Terminal。从搜索结果中启动Terminal应用程序
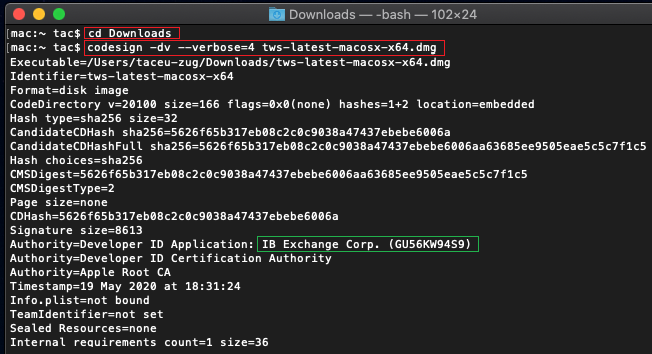
b) 输入cd Downloads然后按Enter键
c) 输入codesign -dv --verbose=4 tws-latest-macosx-x64.dmg然后按Enter键。请注意,文件名称(tws-latest-macosx-x64.dmg)可能会因您下载的TWS版本不同而有所不同。如需要,您可在命令行更换文件名称
d) 检查命令输出,确保“Developer ID Application”是“IB Exchange Corp.”(见下方图4)
图4
3. 运行您下载的TWS安装文件
下载好TWS安装程序并确定文件为原版文件后(上方第1点和第2点),您便可以继续安装了。 这时如果还收到杀毒软件的警告,您可合理相信其为误报并予以忽略。 如果在这一步需要指导,请直接进入下一节。
现在的安全系统都会允许添加例外,正是为了解决误报的问题。 例外规则会强制杀毒软件引擎不对特定文件或程序进行扫描,因而使该特定文件或程序被认为是安全可靠,从而不对其发出警报。
取决于您所使用的安全软件,添加例外情况的程序可能会有所差异。您可以直接从警报弹窗添加临时性或永久性例外,也可以从主配置面板的特定区域手动创建例外。
如果不确定怎么操作,建议您参阅您的杀毒软件文档。
为TWS安装文件或TWS更新程序添加了例外之后,其将不再被阻止,从而能成功完成相应任务。
如果您有理由相信自己的电脑中毒了,我们建议您进行全面的系统扫描。通常,您可以右键点击底部任务栏(Windows)或顶部菜单栏(MacOS)中的杀毒软件图标,届时您会看到一个可以启动全面系统扫描的选项。或者,您也可以从杀毒软件主窗口启动该任务。如果不确定怎么操作,建议您参阅您的杀毒软件文档。
技术背景信息
安全系统如何扫描我从网上下载的文件?
现在的杀毒软件和反恶意软件引擎会根据以下方面识别威胁:
基于签名的扫描:杀毒软件扫描器会搜索之前被归类为恶意或可疑程序的特定字节模式。杀毒软件可能还会比对已知威胁数据库(病毒定义)检查文件签名(哈希)。
行为分析:杀毒软件引擎会探测那些单独拎出来可能不构成威胁、但放在一起与恶意软件活动并无二致的行为(如代码可以复制或隐身、从网上下载其它文件、通过互联网联系外部主机、修改操作系统注册表)。此类扫描旨在发现先前未知的计算机威胁。
启发式探测:扫描器会反向编译代码或在虚拟的限制环境中运行代码。然后其会对照预定义的规则集合对代码的行动进行评估和分类。
基于云端的保护和机器学习:这些都是相对较新的技术。需要分析的文件会发送到杀毒软件/安全系统供应商的云端,在那里会有算法对代码的可靠性和行为进行深度分析。
这些扫描方法绝对可靠吗?
现在的威胁非常复杂狡猾,就像生物病毒一样,可以改变其代码和签名。此外,每天都有新的恶意软件和漏洞利用程序被开发出来并在网上快速传播。因此,上方提到的威胁识别方法并不绝对可靠,但是结合起来使用,它们可以帮助识别绝大多数恶意程序。
尽管基于签名的技术在识别已知威胁方面做得非常成功且不太容易发生误报,但在识别未知的恶意程序和已有恶意程序的变种方面就不那么有效了。在这一领域,行为和启发式方法的表现要好得多,尽管由于它们是基于一定程度的解译而非完全的裸代码匹配,因而存在一定不确定性,从而容易发生误报。
“误报”是指安全系统把无恶意的文件或程序归为恶意文件或程序的情况。
参考:
How to Upload a Diagnostic Bundle from an IBKR Platform
Some support related issues require diagnostics files and logs to be uploaded along with screenshots. The information will help our team to investigate and resolve the issue that you are experiencing.
This article will help you with detailed steps on how to upload diagnostics files and logs from various Interactive Brokers’ trading platforms.
Note: IBKR does not monitor the diagnostic bundle repository throughout the day. Should you spontaneously decide to upload a diagnostic bundle, without being instructed by Interactive Brokers, please inform our Client Services via Message Center ticket or phone call otherwise your error report will go unnoticed.
Please click on one of the links below, according to the platform you are using:
-
IBKR Mobile (Android)
-
IBKR Mobile (iOS)
- For Windows and Linux Operating system: Press Ctrl+Alt+Q
- For Mac: Press Cmd+Option+H






















7. Enter your comments in the field and tap ‘Attach Image’ to attach the screenshot/s you previously saved in your camera roll

A diagnostic trace for Client Portal can be captured following the steps on IBKB3512
关于盈透证券价格限制通知的披露
监管部门期望经纪公司能采取控制措施防止将具有扰乱市场风险(如突然的价格波动)的委托单提交到市场中心。
为此,盈透证券对客户委托单设置了多项价格筛选条件。该等价格筛选条件某些情况下会对客户委托单施以价格限制以避免对市场造成干扰,而该等价格限制通常是IB计算得出的参考价格基础上的一个%浮动范围(价格限制的范围取决于金融产品的类型及其当前价格)。
尽管价格限制是为了在追求交易确定性和最小化价格风险之间寻求平衡,但其可能会导致交易延迟或无法成交。更多信息请参见盈透证券的委托单传递和定单流收入披露。
如果客户的委托单被IB的系统施加了价格限制,则客户会 (i) 在TWS中或通过API或FIX标签58(对于FIX用户)收到价格限制的实时通知;并/或 (ii) 收到每日FYI消息,其中会列出前一日被施加了价格限制的前10笔委托单,包括该等委托单的初步价格限制(如有)和进一步价格限制的限制范围。
客户可以点击FYI消息中的退订链接选择不再接受此类FYI消息。选择退订此类FYI消息即表示客户:
- 同意不再接收盈透证券发出的任何关于对客户委托单应用了价格限制的通知;并且
- 确认客户已经了解,客户的委托单未来可能会被施加价格限制,但客户不想再就其委托单被施加了价格限制收到任何通知。
交易平台登录失败故障排除
c. 端口4000/4001被禁。在酒店、咖啡厅等公共网络环境下这些端口常常无法访问,因此需解锁这些端口来应用入站/出站TCP协议。此外,如果您的电脑连接了路由器,则路由器上也需打开这些端口。*
临时安全码有效期是多久?
对于加入安全登录系统的客户,如果其安全设备找不到、遗失或损坏,IBKR会提供临时密码。客户可在2天内使用此临时密码访问客户端和交易平台。2天后,临时密码便不再能用于访问交易平台,但仍可在8天内供客户访问客户端。但客户端的访问权限仅限于打印或保存在线安全代码卡。
而在线安全代码卡则有21天有效期,可以让账户持有人有时间找出设备,或者如果是设备遗失或损坏导致需要更换也可在收到更换设备前继续访问账户。没有实物安全设备又无法使用临时密码或在线安全代码卡登录的账户持有人要访问账户需联系客户服务(ibkr.com/support)。
恢复账户永久性访问的最快办法是安装并激活采用IB Key的移动IBKR程序。有关此智能手机程序激活的详细信息,请参见此处。
重要通知
根据政策,IBKR将不再为账户连续提供临时密码,而是会通过实物安全设备将账户保护提高至最安全等级。
参考链接
- KB70:请求临时密码的说明
- KB1131:安全登录系统概述
- KB2636:安全设备相关信息与程序
- KB2481:在两个或以上使用者之间共享安全登录设备的说明
- KB2545:退出后再参加安全登录系统的说明
- KB975:如何将安全设备退还给IBKR
- KB2260:通过移动IBKR激活IB Key验证的说明
- KB2895:多重双因素验证系统(M2FS)
- KB1861: 安全设备更换费用
Disclosure Regarding Interactive Brokers Price Cap Notices
Regulators expect brokerage firms to maintain controls designed to prevent the firm from submitting orders to market centers that create a risk of disruptive trading (e.g., the risk of sudden, transient price moves).
To comply with these expectations, Interactive Brokers implements various price filters on customer orders. Those price filters may, in certain circumstances, price cap customer orders in order to avoid market disruption, and those Price Caps will generally be in a % range from a reference price range calculated by IB. (The range of the Price Cap varies depending on the type of instrument and the current price.)
Although the price caps are intended to balance the objectives of trade certainty and minimized price risk, a trade may be delayed or may not take place as a result of price capping. More information is available in Interactive Broker’s Order Routing and Payment for Order Flow Disclosure.
If a customer’s order(s) are price capped by IB’s systems, that customer will either receive (i) real-time notification of those price cap(s) in Trader Workstation or via the API or FIX tag 58 (for FIX users); and/or (ii) a daily FYI message containing a digest of the first 10 order(s) that were price capped the prior day, the initial price cap(s) for those order(s) (if applicable), and the Price Cap Range(s) for further Price Cap(s) of those order(s).
Customers may opt out from receiving future FYI Messages by clicking the relevant opt-out link within an FYI Message. By opting out from receiving these future FYI Messages, a customer:
- Agrees to waive any further notifications from Interactive Brokers about the application of the firm’s Price Caps to that customer’s order(s); and
- Acknowledges that he or she understands that his or her orders may be price-capped in the future, but that the customer does not wish to be notified again about the application of any Price Caps to any of his or her orders.
Possible Alerts during the TWS installation or update
IBKR's Trader Workstation (TWS) is a global trading system enabling clients to use a suite of online trading tools. The TWS can be installed on Windows, Mac OS X and Linux, and it requires the presence of a Java Runtime Environment (JRE). Therefore, when you install the TWS, it also downloads the necessary Java files in order to run using a Java Virtual Machine (JVM).
Sometimes, during the installation or update process of the TWS, software such as Antivirus applications will show an alert and prevent the process to complete. The warning and other messages in this case can safely be ignored, and you can complete the installation of the trading platform.
Table of content
Downloading the TWS installer and update patches
The TWS installers available in the download areas of ibkr.com or IBKR regional web sites are sealed and digitally signed using all the safety procedures required by the industry standards and do not contain any malicious code or process. The same industry standard practices have been used for the TWS update patches, which are automatically downloaded and installed when launching the TWS (if and only if there is an update available). Nevertheless, if you have received an alert, we recommend you to be cautious. Should you intend to keep the TWS installation file on your machine for future use, you should make sure that the same precautions for the protection of data from viruses and malware are applied to it.
Why do I receive a warning when I install the TWS or when the TWS automatic update runs?
You might see an alert (similar to Figure 1 but not limited to) and your security system would wait for your input on how to process the suspicious file. You usually have the option to quarantine the file, delete it, ignore it once or create a permanent exception for it.
Please note that your antivirus might autonomously quarantine or delete the TWS installer file or some of his components without asking for your confirmation and without showing you any warning. Nevertheless, this should only happen if you have preset your antivirus to specifically react in this way.
Figure 1.

What should I do when I receive a warning?
In case you receive a warning during the TWS installation or update, we recommend the following steps:
1. Delete the TWS installer and download it again from the IBKR main or regional web site
a) Delete the TWS installer file already present on your computer and then delete it as well from your Trash (empty your Trash)
b) From the table below, click on the TWS download area correspondent to your location
| Location | TWS download area |
| US | https://www.ibkr.com |
| Asia / Oceania | https://www.interactivebrokers.com.hk |
| India | https://www.interactivebrokers.co.in |
| Europe | https://www.interactivebrokers.co.uk https://www.interactivebrokers.eu |
c) Check the website certificate. Most Internet browsers will immediately alert you in case the site certificate is invalid, compromised or expired. Nevertheless, if you want to check manually the validity of the site certificate, click on the padlock close to the address (URL) and make sure the Connection is reported as secure and no security warning are present (see Figure 2 below).
Figure 2.

d) Click on the button labeled with the TWS version you wish to use and download again the TWS installer
2. Check the digital signature of the TWS installer file you have downloaded
Normally you will immediately receive a security warning in case the digital signature of a file is compromised. Nevertheless, if you wish to perform a manual check, proceed as follows, according to your Operating System:
For Windows
a) From the Windows file explorer, access your Downloads folder or the folder where you placed the TWS installer
b) Right click on the TWS installer file, select Properties and then click on the tab "Digital Signatures"
c) Click on "Details" and on "View Certificate" to check the certificate status and signer. The legitimate signer is "IB Exchange Corp." (See Figure 3 below)
Figure 3.

For Mac OS X
a) Click on the magnifier glass (Spotlight Search) on the top right of your screen and type Terminal. From the search results, launch the Terminal app
b) Type cd Downloads and press Enter
c) Type codesign -dv --verbose=4 tws-latest-macosx-x64.dmg and press Enter. Please notice that the name of the file (tws-latest-macosx-x64.dmg) may differ according to the TWS version you decided to download. If needed, replace the file name in the command with the appropriate one
d) Check the command output and make sure the "Developer ID Application" is "IB Exchange Corp." (see Figure 4 below)
Figure 4.

3. Run the TWS installer file you have downloaded
Once you have downloaded again the TWS installer and after you made sure the file is original (points 1. and 2. above), you can proceed with the installation. Should you still receive a warning from your antivirus, you can reasonably consider it as a false positive and ignore it. Should you need guidance on this step, please proceed directly to the next section.
How can I signal an Alert as false positive?
All modern security systems allow the creation of exceptions, precisely in order to address false positive cases. An exception is a rule forcing the antivirus engine not to scan a specific file or process. That specific file or process will hence be deemed safe and no further alerts will be raised for it.
The procedure for creating an exception may vary, according to the security software you are using. You may be able to create a temporary or permanent exception directly from the alert pop-up or you may have to create one manually from a specific section in the main configuration panel.
If you are unsure of the procedure, we recommend you to consult your antivirus documentation.
Once you have set an exception for the TWS installer file or for the TWS updater process, those will be no longer blocked and will be able to complete their respective tasks successfully.
What else can I do if I have doubts or if my system behaves abnormally?
If you have reasons to believe your machine may be compromised or infected, we recommend performing a full system scan. Usually you can right click on the antivirus icon present on the bottom taskbar (for Windows) or on the upper menu bar (for MacOS) and you will find the option to launch a full system scan. Alternatively, you may start that task from the main antivirus window. If you are unsure of the procedure, we recommend you to consult your antivirus documentation.
Technical Background
How does my security system scan the files I download from the Internet?
Modern antivirus and anti-malware engines base their threats recognition on:
Signature-based scanning: the antivirus scanner searches for a specific pattern of bytes that was previously catalogued as malicious or at least suspicious. The antivirus may check as well file signatures (called hash) against a database of known threats (called virus definitions).
Analysis of behavior: the antivirus engine detects specific actions which individually may not represent a threat but, when correlated together, resemble the usual activity of a malicious software (e.g. the ability of a code to replicate or hide itself, download additional files from the Internet, contact external hosts over the Internet, modify the Operating System registry) This type of scan is designed to detect previously unknown computer threats.
Heuristic detection: the scanner de-compiles the code or runs it within a virtual, restricted environment. It then classifies and weights the actions performed by the code against a predefined, behavior based, rule set.
Cloud-based protection and machine learning: those are relatively new techniques. The file that needs to be analyzed is sent to the antivirus / security system vendor cloud where sophisticated algorithms perform a deep analysis of the code authenticity and behavior.
Are those scan methods infallible?
Modern threats are very sophisticated and, like biological viruses, can mutate their code and their signatures. Moreover, new malwares and exploits are created every day and spread rapidly over the Internet. The threat recognition methods mentioned above are therefore not infallible but can guarantee a high percentage of malware recognition when combined together.
While signature based techniques are very successful in recognizing known threats and less prone to false positives, they are not so efficient in recognizing unknown malware or mutations of existing ones. In this area, the behavioral and heuristic methods perform much better although they are more prone to false positives since their detection is not based on bare code matching but on a certain degree of interpretation and hence uncertainty.
The term "false positive" is used when a security system classifies an innocuous file or process as malware.
Reference:
Alternative Streaming Quotes for US Equities
The SEC Vendor Display Rule requires that brokers give clients access to the NBBO at the point of order entry. In order to provide users with free live streaming market data, we cannot display this free stream when entering an order without the client subscribing to the paid NBBO. Please note, this does not apply to non-IBLLC clients.
Under the Rule 603(c) of Regulation NMS (Vendor Display Rule), when a broker is providing quotation information to clients that can be used to assess the current market or the quality of trade execution, reliance on non-consolidated market information as the source of that quotation would not be consistent with the Vendor Display Rule.
All clients (IBKR Lite and Pro) have access to streaming real-time US equity quotes from Cboe One and IEX at no charge. Since this data does not include all markets, we cannot show this quote when entering parameters for a US stock quote. Therefore and according to FINRA's enforcement of the SEC rule, IBKR provides IBLLC US clients a free default snapshot service, “US Snapshots VDR Required”. If clients do not sign up for an NBBO US equity data service and they are an IBLLC client, they will have access to free real-time snapshots when making trading decisions on US stocks. Order routing will not change based on what is shown on the screen. If one is subscribed to NBBO quotes or not, by default the trade will still take place with the assistance of the SMART order router designed to provide the best price for the order.
Please see the sample screenshots below from TWS Classic and TWS Mosaic for what occurs when placing an order without the NBBO streaming subscription for US equities.
TWS Classic:
1. Screenshot of quotes showing without order entry line item
2. Screenshot of quote going blank when putting in the order entry line item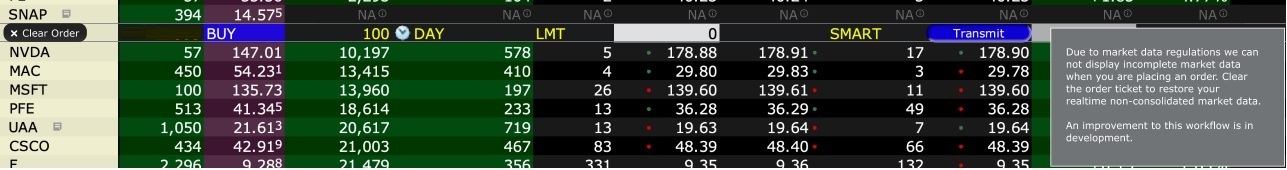
TWS Mosaic:
1. Screenshot of quotes showing without order entry line item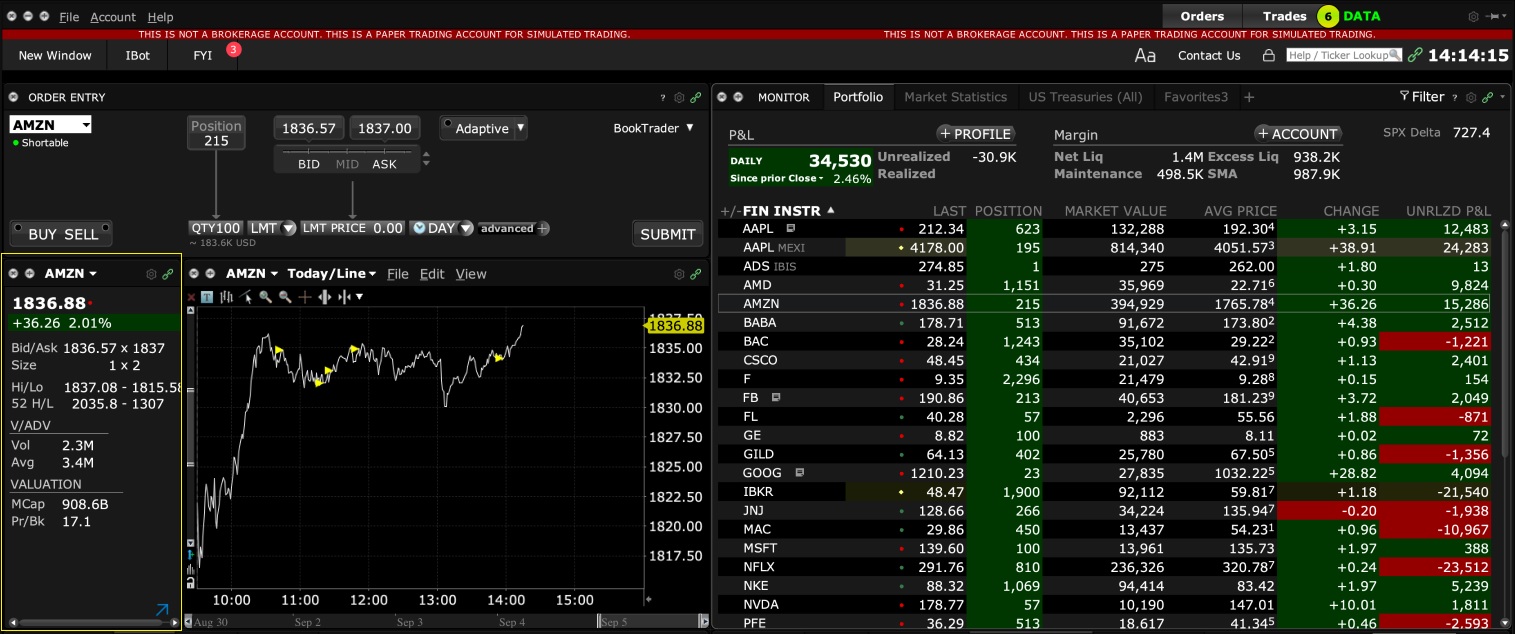
2. Screenshot of quote going blank when putting in the order entry line item